CCNA Interview Questions and Answers: CCNA is a renowned IT certification from Cisco, focusing on networking skills. It validates the ability to handle enterprise networks, including installation, configuration, operation, and troubleshooting. CCNA is highly valued by top IT companies and serves as a foundation for networking careers.
This article presents a compilation of the Latest CCNA Interview Questions for freshers, including a comprehensive list of the top 75 CCNA interview questions and their corresponding answers. It serves as a valuable resource to prepare for CCNA Technical Interview Questions.
★★ Latest Technical Interview Questions ★★
CCNA Technical Interview Questions
Boost your interview readiness with this collection of the Top 75 CCNA interview questions and answers. Whether you’re a beginner or experienced, it provides valuable insights to excel in your CCNA interview preparation. Enhance your confidence and knowledge with the latest CCNA interview questions.
Top 75 CCNA Interview Questions and Answers
1. What is the purpose of a subnet mask in IP networking?
A subnet mask is used to divide an IP network into subnetworks by determining the network and host portions of an IP address.
2. Explain the difference between a hub and a switch.
A hub operates at the physical layer of the OSI model and broadcasts incoming data to all connected devices, while a switch operates at the data link layer and forwards data only to the intended recipient based on MAC addresses.
3. What do you mean by 100BaseFX?
100BaseFX is an Ethernet media standard that utilizes fiber optic cables instead of twisted-pair cables. It is a variant of Fast Ethernet designed for high-speed data transmission within local area networks (LANs) at a rate of 100 Mbps. The “FX” signifies the use of fiber optic cables as the primary transmission medium in this configuration.
4. What is the purpose of a default gateway in a network?
The default gateway is the IP address of the router that connects a local network to external networks. It serves as the exit point for traffic destined for networks outside the local subnet.
5. Describe the difference between TCP and UDP protocols.
TCP (Transmission Control Protocol) is a connection-oriented protocol that ensures reliable, ordered, and error-checked delivery of data, while UDP (User Datagram Protocol) is a connectionless protocol that provides faster but unreliable delivery of data.
6. Name types of routes that are available in routers
Types of routes available in routers include:
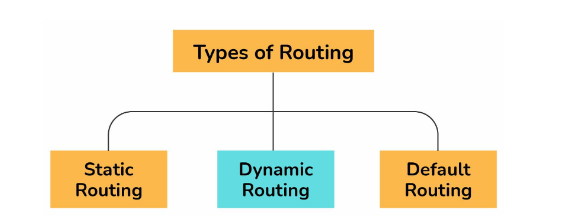
Static Route:
- Also known as a non-adaptive route.
- Configured directly on an active interface or manually added to the routing table.
Default Route:
- Sends all packets to a single router, regardless of the specific network.
- Useful for networks with a single exit point.
Dynamic Route:
- Also known as an adaptive route.
- Automatically adjusts routes based on the current state in the routing table.
- Utilizes routing protocols to find network destinations.
7. What is the significance of the OSI model in networking?
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of networking protocols, allowing different systems to communicate and interoperate across networks.
8. How does ARP (Address Resolution Protocol) work?
ARP resolves IP addresses to MAC addresses by broadcasting an ARP request on the network, and the device with the corresponding IP responds with its MAC address, allowing communication at the data link layer.
9. Explain the concept of VLAN (Virtual Local Area Network).
VLANs logically divide a physical LAN into multiple virtual LANs, enabling network segmentation, improved security, and efficient network management by grouping devices based on their functional or departmental requirements.
10. What do you mean by a broadcast domain and a collision domain?
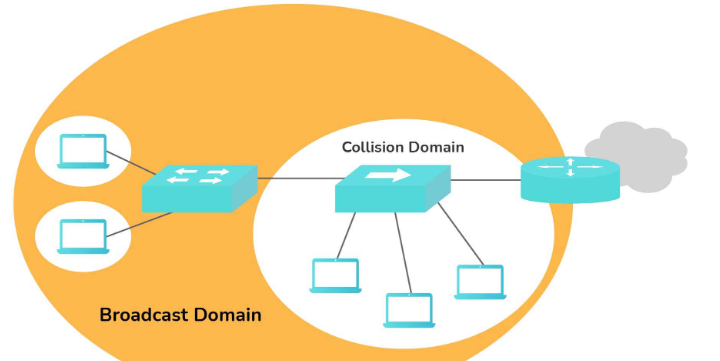
Broadcast Domain:
- The logical set of reachable computer systems without a router.
- Traffic flows throughout the network.
- Broadcast messages are received by all devices in the broadcast domain.
Collision Domain:
- Part of a network where packet collisions can occur.
- Collisions happen on shared mediums or through repeaters.
- All devices in the collision domain receive messages, regardless of the destination.
11. What is the purpose of NAT (Network Address Translation)?
NAT translates private IP addresses to public IP addresses and vice versa, enabling devices in a private network to access the internet using a shared public IP address, conserving IPv4 address space.
12. Describe the process of DHCP (Dynamic Host Configuration Protocol).
DHCP dynamically assigns IP addresses, subnet masks, default gateways, DNS server addresses, and other network configuration parameters to devices on a network, simplifying the process of network configuration.
13. How does STP (Spanning Tree Protocol) prevent network loops?
STP eliminates loops in Ethernet networks by selecting a root bridge and blocking redundant paths, allowing a loop-free logical topology to be created, ensuring network stability and preventing broadcast storms.
14. What is the function of a router in a network?
A router is a networking device that connects multiple networks together and forwards packets between them based on their destination IP addresses. It determines the best path for data transmission and enables communication between different networks.
15. What are three possible ways of data transmission in CCNA?
Three possible ways of data transmission in CCNA include:
Simplex: In Simplex mode, communication is unidirectional, similar to a one-way road. Only one of the two devices on a connection can transmit data, while the other can only receive it. Simplex mode allows for the full capacity of the channel to be utilized for one-way data transmission.
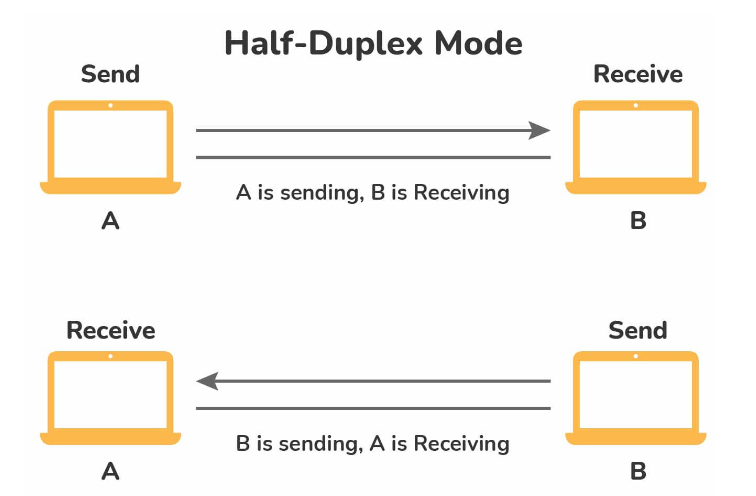
Half Duplex: In Half-duplex mode, each station has the capability to both transmit and receive, but not at the same time. When one device is sending data, the other can only receive, and vice versa. This mode is commonly used in situations where simultaneous two-way communication is not necessary. The entire capacity of the channel can be utilized for each direction of data transmission.
Full Duplex: In Full-duplex mode, both stations have the ability to simultaneously send and receive data. The capacity of the connection is shared between signals going in different directions. This sharing can occur in two ways:
- The connection consists of two separate transmission paths, one for sending and one for receiving.
- The capacity is divided between signals going in both directions.

16. Explain the difference between static and dynamic routing.
Static routing involves manually configuring the routing table on a router, where routes are entered manually and do not change unless modified. Dynamic routing, on the other hand, uses routing protocols to dynamically exchange routing information among routers, allowing the network to adapt to changes automatically.
17. How does ICMP (Internet Control Message Protocol) work?
ICMP is a network protocol used to send error messages and operational information regarding IP packet transmission. It is primarily used for diagnostic and troubleshooting purposes, such as checking if a destination is reachable or reporting errors.
18. Describe the purpose of access control lists (ACLs) in networking.
ACLs are used to control network traffic by filtering packets based on specified criteria, such as source/destination IP addresses, protocols, ports, or other parameters. They can be configured to permit or deny traffic, providing security and traffic management capabilities.
19. What is the purpose of DNS (Domain Name System)?
DNS is a hierarchical naming system that translates domain names (e.g., www.example.com) into IP addresses. It allows users to access resources on the internet using domain names, simplifying the process of locating and connecting to websites and other network services.
20. Explain the difference between a broadcast domain and a collision domain.
| Broadcast Domain | Collision Domain |
|---|---|
| Group of devices that receive each other’s broadcast messages | Group of devices where network collisions can occur |
| Broadcast messages are forwarded within the domain | Collisions can happen when two devices transmit data simultaneously |
| Defined by switches, routers, and VLANs | Defined by shared Ethernet segments (hubs, repeaters) |
| Broadcast traffic does not pass through routers | Collisions are limited to devices on the same segment |
21. Explain the concept of port forwarding.
Port forwarding, also known as port mapping, is a technique used to redirect incoming network traffic from one IP address and port to another. It is commonly used to enable access to services hosted on private networks from the internet by mapping a public IP/port to a specific internal IP/port.
22. How does OSPF (Open Shortest Path First) routing protocol function?
OSPF is an interior gateway protocol that uses link-state routing to calculate the shortest path to a destination network. Routers exchange link-state advertisements (LSAs) to build a topology map and determine the best path based on metrics such as cost, allowing for efficient routing in large networks.
23. Describe the purpose of a firewall in network security.
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between internal and external networks, enforcing security policies to protect against unauthorized access and potential threats.
24. What is the purpose of a loopback address?
A loopback address, typically represented as 127.0.0.1 in IPv4, is a special IP address assigned to the loopback interface of a device. It allows a device to send network packets to itself for testing network functionality without involving the physical network.
25. How does VLAN (Virtual Local Area Network) differ from a subnet?
| VLAN | Subnet |
|---|---|
| Logical segmentation of a single physical network | Division of a network into smaller IP address ranges |
| Operates at the data link layer (Layer 2) | Operates at the network layer (Layer 3) |
| Separates traffic based on VLAN membership | Separates traffic based on IP address boundaries |
| Provides broadcast domain isolation | Defines IP address boundaries and routing behavior |
| Enables network flexibility and security | Facilitates efficient IP address allocation and routing |
26. Explain the concept of subnetting in IP networking.
Subnetting is the process of dividing a large IP network into smaller subnetworks, known as subnets. It helps optimize network resources, improve security, and provide hierarchical addressing by allocating a portion of the host bits in an IP address to define subnets.
27. What is the syntax to assign an IP address to an interface in Cisco IOS?
To assign an IP address to an interface, use the following command:
interface <interface-name> followed by ip address <ip-address> <subnet-mask>.
28. How do you configure a default gateway on a Cisco router using the command line interface?
To configure a default gateway, use the command
ip default-gateway <gateway-ip-address>.
29. What is the difference between a router and a switch in a network?
| Router | Switch |
|---|---|
| Operates at the network layer (Layer 3) | Operates at the data link layer (Layer 2) |
| Routes traffic between different networks | Forward traffic within a single network |
| Makes decisions based on IP addresses and routing tables | Makes decisions based on MAC addresses and forwarding tables |
| Provides interconnectivity for multiple networks | Provides connectivity to devices within a network |
30. What is the syntax to enable OSPF (Open Shortest Path First) routing protocol on a Cisco router?
To enable OSPF, enter the global configuration mode and use the command
router ospf <process-id>.
31. How do you configure VLANs (Virtual Local Area Networks) on a Cisco switch?
To configure VLANs, go to the global configuration mode and use the command vlan <vlan-id>. Repeat this command for each VLAN you want to create.
32. What is the syntax to configure port security on a Cisco switch interface?
To configure port security, go to the interface configuration mode and use the command switchport port-security.
33. What are the differences between TCP and UDP protocols?
| TCP (Transmission Control Protocol) | UDP (User Datagram Protocol) |
|---|---|
| Connection-oriented protocol | Connectionless protocol |
| Provides reliable and ordered data delivery | Does not guarantee reliable delivery or order |
| Implements flow control and error recovery | No flow control or error recovery mechanisms |
| Slower but more reliable | Faster but less reliable |
| Used for applications such as web browsing, email | Used for applications such as video streaming, gaming |
34. How do you configure an access control list (ACL) on a Cisco router?
To configure an ACL, enter the global configuration mode and use the command access-list <acl-number> {permit|deny} <source> <destination>.
35. What is the syntax to enable SSH (Secure Shell) on a Cisco device?
To enable SSH, go to the global configuration mode and use the command ip ssh version 2 followed by crypto key generate rsa.
36. How does static routing differ from dynamic routing?
| Static Routing | Dynamic Routing |
|---|---|
| Manual configuration of routing tables | Automatic learning and updating of routing tables |
| Requires manual intervention for changes | Adapts to network changes dynamically |
| Best suited for small and simple networks | Ideal for large and complex networks |
| Less overhead on network resources | Requires more processing power and bandwidth |
| Limited scalability and flexibility | Offers scalability and adaptability |
37. How do you configure NAT (Network Address Translation) on a Cisco router?
To configure NAT, go to the global configuration mode and use the command ip nat inside source <inside-local> <inside-global>.
38. What is the syntax to configure EtherChannel (link aggregation) on a Cisco switch?
To configure EtherChannel, go to the interface configuration mode and use the command channel-group <channel-group-number> mode <mode>.
39. How do you configure DHCP (Dynamic Host Configuration Protocol) on a Cisco router?
To configure DHCP, go to the global configuration mode and use the commandip dhcp pool <pool-name> followed by the necessary DHCP parameters.
40. What are the differences between IPv4 and IPv6 addressing?
| IPv4 | IPv6 |
|---|---|
| 32-bit address format | 128-bit address format |
| Limited address space (approximately 4.3 billion addresses) | Expansive address space (approximately 3.4 x 10^38 addresses) |
| Uses decimal notation (e.g., 192.168.1.1) | Uses hexadecimal notation (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334) |
| Does not provide built-in security features | Includes built-in IPsec for enhanced security |
41. How does VTP (VLAN Trunking Protocol) work?
- VTP allows for centralized VLAN configuration and distribution.
- It synchronizes VLAN information between switches.
- Reduces manual configuration efforts in managing VLANs.
42. What is the difference between half-duplex and full-duplex communication?
- In half-duplex communication, data can be transmitted in both directions, but not simultaneously.
- In full-duplex communication, data can be transmitted simultaneously in both directions.
43. Explain the differences between half-duplex and full-duplex communication.
| Half-Duplex | Full-Duplex |
|---|---|
| Communication in one direction at a time | Simultaneous communication in both directions |
| Devices take turns transmitting and receiving | Devices can transmit and receive simultaneously |
| Inefficient for high-bandwidth applications | Suitable for high-bandwidth applications |
| Examples include walkie-talkies, old Ethernet networks | Examples include modern Ethernet networks, telephone systems |
44. What is the purpose of a MAC address in networking?
- A MAC address is a unique identifier for a network device.
- It identifies devices at the data link layer.
- It facilitates communication within a local network.
45. Explain the concept of link aggregation or EtherChannel.
- Link aggregation, also known as EtherChannel or port-channel, combines multiple physical networks links into a single logical link.
- It increases bandwidth, improves redundancy, and provides load-balancing capabilities.
46. How does HSRP (Hot Standby Router Protocol) provide redundancy?
- HSRP allows multiple routers to work as virtual routers with a single virtual IP address.
- If the active router fails, another router within the HSRP group takes over the virtual IP address to ensure continuous connectivity.
47. What is the difference between a hub and a switch?
| Hub | Switch |
|---|---|
| Operates at the physical layer (Layer 1) | Operates at the data link layer (Layer 2) |
| Broadcasts incoming data to all connected devices | Forwards data selectively to the intended device |
| Does not perform any filtering or addressing | Performs MAC address learning and filtering |
| Shared bandwidth among connected devices | Dedicated bandwidth for each port |
| Prone to collisions and limited performance | Provides improved performance and network efficiency |
48. What is the role of a DHCP relay agent in network communication?
- A DHCP relay agent forwards DHCP messages between clients and DHCP servers on different subnets.
- It enables DHCP clients in one subnet to obtain IP configuration information from servers in another subnet.
49. What is the purpose of a network mask in IPv6 networking?
- In IPv6 networking, a network mask, or prefix length, identifies the network portion of an IP address.
- It helps determine routing and addressing within the IPv6 network.
50. Explain the concept of QoS (Quality of Service) in network traffic management.
- QoS prioritizes and manages network traffic based on specific criteria.
- It ensures that critical applications or services receive sufficient network resources to meet their performance requirements.
51. What are the distinctions between access control lists (ACLs) and firewall rules?
| Access Control Lists (ACLs) | Firewall Rules |
|---|---|
| Operate at the network layer (Layer 3) | Can operate at both network and transport layers |
| Filter traffic based on source and destination IP addresses | Filter traffic based on multiple criteria such as source/destination IP, port numbers, protocols |
| Applied to interfaces on routers and switches | Implemented on dedicated firewall appliances or software |
| Provide basic traffic filtering and control | Offer advanced security features and policies |
52. How does EIGRP (Enhanced Interior Gateway Routing Protocol) function?
- EIGRP exchanges routing information with neighboring routers.
- It calculates the best paths based on metrics such as bandwidth, delay, and reliability.
- EIGRP provides rapid convergence and supports VLSM (Variable Length Subnet Masking).
53. What is the purpose of a proxy server in network communication?
- A proxy server acts as an intermediary between clients and servers.
- It handles client requests and forwards them to the appropriate server.
- Proxy servers provide caching, filtering, access control, and anonymity services.
54. What is the difference between a layer 2 and a layer 3 switch?
| Layer 2 Switch | Layer 3 Switch |
|---|---|
| Operates at the data link layer (Layer 2) | Operates at the network layer (Layer 3) |
| Forwards traffic based on MAC addresses | Forwards traffic based on IP addresses |
| Provides basic switching functionality | Offers both switching and routing capabilities |
| Manages VLANs and performs MAC address learning | Supports VLANs, routing protocols, and access control |
| Limited to local network connectivity | Facilitates inter-VLAN routing and network segmentation |
55. Explain the concept of VLAN trunking and tagging.
- VLAN trunking involves carrying multiple VLANs over a single physical link between switches.
- Tagging adds a VLAN identifier to the Ethernet frame, allowing switches to distinguish and forward VLAN traffic appropriately.
56. How does VRRP (Virtual Router Redundancy Protocol) provide high availability?
- VRRP enables multiple routers to work together as a virtual router with a single virtual IP address.
- If the active router fails, another router within the VRRP group takes over the virtual IP address, ensuring continuous connectivity.
57. Describe the purpose of an NTP (Network Time Protocol) server.
An NTP server synchronizes the time across devices in a network, ensuring accurate timekeeping and synchronization for various network functions and applications.
58. What is the function of a network bridge in connecting LAN segments?
- A network bridge connects multiple LAN segments and forwards data between them at the data link layer.
- It enables communication and segmentation within a network while reducing broadcast traffic.
59. Explain the concept of multicast communication in network protocols.
- Multicast communication allows for the efficient transmission of data from one sender to multiple receivers simultaneously.
- It minimizes network bandwidth usage by delivering data only to interested recipients in a multicast group.
60. How does IPsec (Internet Protocol Security) provide secure communication?
- IPsec is a protocol suite that encrypts and authenticates IP packets, ensuring secure communication over IP networks.
- It provides confidentiality, integrity, and authentication services for IP-based communication.
61. Describe the purpose of a load balancer in distributing network traffic.
- A load balancer evenly distributes incoming network traffic across multiple servers or resources.
- It improves scalability, availability, and performance by optimizing resource utilization and preventing overload on individual servers.
62. What is the significance of the TTL (Time to Live) field in IP packets?
- The TTL field in IP packets specifies the maximum time a packet can exist in a network before being discarded.
- It prevents packets from circulating indefinitely and helps manage network congestion.
63. Explain the concept of DHCP snooping in network security.
- DHCP snooping is a security mechanism that prevents unauthorized DHCP servers from providing IP configuration to clients.
- It ensures that only trusted DHCP servers are used and helps prevent network attacks, such as IP address spoofing.
64. How does IGMP (Internet Group Management Protocol) function in multicast communication?
- IGMP is a network-layer protocol used by hosts and adjacent routers to manage and control multicast group membership.
- It allows hosts to join or leave multicast groups dynamically and enables efficient delivery of multicast traffic within a network.
65. Describe the purpose of a content delivery network (CDN) in network performance.
- A CDN is a distributed network of servers strategically placed at different locations to deliver web content more efficiently to users.
- It improves network performance by reducing latency, minimizing bandwidth usage, and enhancing content availability and reliability.
66. What is the function of a network tap in monitoring network traffic?
- A network tap is a device that monitors network traffic by capturing and forwarding network packets for analysis and monitoring purposes.
- It allows network administrators to analyze network behavior, detect anomalies, and troubleshoot network issues.
67. What is the purpose of a wireless access point in a network?
- A wireless access point (WAP) enables wireless devices to connect to a wired network.
- It serves as a central hub for wireless communication, allowing devices to access network resources and connect to the internet wirelessly.
68. Explain the concept of port security in switch configuration.
- Port security is a feature that restricts access to switch ports based on MAC addresses.
- It helps prevent unauthorized access by allowing only specific devices or MAC addresses to connect to a particular switch port.
69. How does MPLS (Multi-Protocol Label Switching) work?
- MPLS is a routing technique that uses labels to efficiently forward data packets across networks.
- It assigns labels to packets, creating label-switched paths (LSPs) that simplify and speed up the routing process.
70. Describe the purpose of a VPN (Virtual Private Network).
- A VPN establishes secure and encrypted connections over a public network, such as the Internet.
- It allows users to access private networks remotely and ensures privacy, confidentiality, and data integrity during transmission.
71. What is the function of a DNS server in network name resolution?
- A DNS server translates domain names (e.g., www.example.com) into IP addresses (e.g., 192.168.1.1) for network communication.
- It resolves human-readable domain names to their corresponding IP addresses, facilitating the routing of data across the internet.
72. Explain the concept of packet fragmentation in IP networking.
- Packet fragmentation breaks larger IP packets into smaller fragments to accommodate networks with smaller maximum transmission unit (MTU) sizes.
- It allows data to be transmitted across networks with varying packet size limits, reassembling the fragments at the destination.
73. How does BGP (Border Gateway Protocol) function in internet routing?
- BGP is a routing protocol used to exchange routing information between different autonomous systems (AS) on the internet.
- It enables routers to determine the best path for forwarding traffic based on policies and reachability information.
74. Describe the purpose of SNMP (Simple Network Management Protocol).
- SNMP is a protocol used for network management and monitoring.
- It allows network administrators to monitor and manage network devices, retrieve information, and receive notifications about network events.
75. What is the significance of CIDR (Classless Inter-Domain Routing) in IP addressing?
- CIDR is a method used to allocate and assign IP addresses more efficiently.
- It allows for more flexible address space allocation by allowing variable-length subnet masks, resulting in better address space utilization and more efficient routing
The article “Top 75 CCNA Interview Questions and Answers” offers a comprehensive guide for CCNA technical interviews, covering installation basics to advanced concepts. It is a valuable resource for job seekers looking to prepare for CCNA interviews. Follow us at freshersnow.com for more insights.