
Cyber Security Interview Questions and Answers: Cybersecurity protects internet-connected systems from attacks, including computers, networks, and data. It involves technologies and practices to safeguard against unauthorized access and attacks. Cybersecurity aims to secure computing resources and online information from potential threats.
To succeed in Cyber Security Interview, it is important to have a solid command of the most recent Cybersecurity interview questions. Our collection of the Top 100 Cybersecurity Interview Questions and Answers is designed to assist you in achieving this objective. Covering a wide range of topics and scenarios, these resources will enhance your knowledge and preparation for Cybersecurity interviews.
★★ Latest Technical Interview Questions ★★
Cyber Security Technical Interview Questions
This article offers a comprehensive list of the latest Top 100 Cybersecurity Interview Questions and Answers. It covers a wide range of topics, including Cyber Security Technical Interview Questions and Cyber Security Interview Questions for Freshers, providing valuable insights to help candidates enhance their knowledge and excel in their interviews.
Top 100 Cyber Security Interview Questions and Answers
1. What is the difference between vulnerability, threat, and risk?
- Vulnerability refers to a weakness or flaw in a system that could be exploited.
- A threat is a potential danger or harm that can exploit vulnerabilities.
- Risk is the likelihood of a threat exploiting a vulnerability and the potential impact it can have.
2. Explain the concept of defense in depth in Cybersecurity.
Defense in depth is an approach that involves using multiple layers of security controls to protect against various types of attacks. It includes measures like firewalls, intrusion detection systems, encryption, access controls, and regular security updates.
3. What are the common types of encryption algorithms used in securing data?
Common encryption algorithms include Advanced Encryption Standard (AES), Rivest Cipher (RC), Data Encryption Standard (DES), Triple DES (3DES), and RSA (Rivest-Shamir-Adleman).
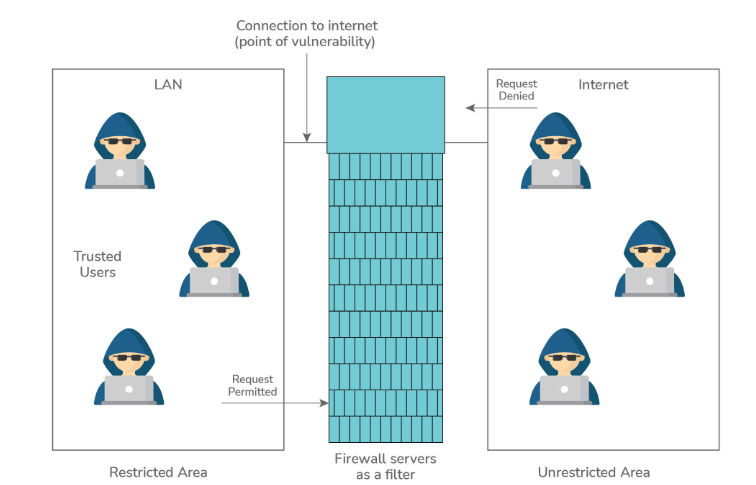
4. What is a Firewall?
A firewall acts as a protective barrier between a local area network (LAN) and the Internet. Its purpose is to maintain the privacy of internal resources while mitigating security risks. The firewall controls the flow of network traffic, both incoming and outgoing, and can employ a combination of hardware and software to filter and monitor the data at the point of connection between the LAN and the Internet, which is the vulnerable point.
There are two types of firewall systems: one that uses network layer filters and the other that uses user, application, or network layer proxy servers
5. Define the term “phishing” and explain how it can be prevented.
Phishing is a cyber-attack where attackers impersonate legitimate entities to deceive individuals into revealing sensitive information. It can be prevented through user awareness training, being cautious of suspicious emails or messages, and verifying the authenticity of requests before sharing any personal information.
6. Define VPN.
A VPN, short for virtual private network, is a secure connection that allows you to connect your computer to a private network through the Internet. It establishes an encrypted link, ensuring the confidentiality of your data and hiding your IP address. By using a VPN, you can safely share information, access the internet, and protect your online identity. VPN technology is commonly utilized in corporate environments and enables secure remote work.
7. What is the role of a firewall in network security?
A firewall acts as a barrier between internal networks and external networks, monitoring and controlling incoming and outgoing network traffic based on predefined security rules. It helps prevent unauthorized access and protects against malicious activities by filtering and blocking potentially harmful traffic.
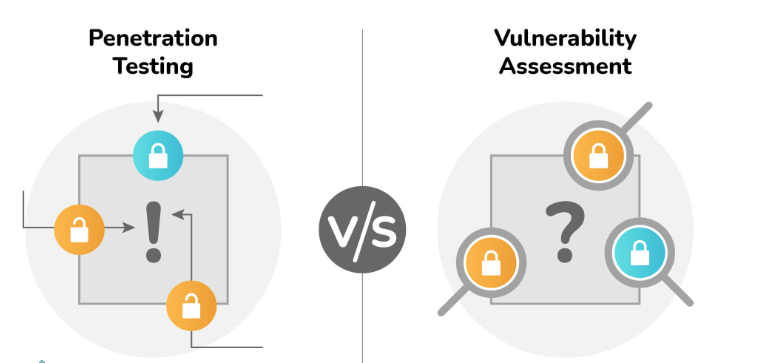
8. Differentiate between Vulnerability Assessment and Penetration Testing.
- Vulnerability assessment and penetration testing are distinct methodologies that share a common objective: enhancing network security by identifying and addressing vulnerabilities within the network environment.
- Vulnerability Assessment is a systematic process that involves identifying, detecting, and prioritizing vulnerabilities in computer systems, network infrastructure, applications, and other systems. It aims to provide organizations with valuable information to address these weaknesses and enhance their overall security posture.
- Penetration Testing, also known as ethical hacking or pen-testing, is a proactive method used to identify vulnerabilities in networks, systems, applications, or other systems. Its objective is to prevent potential attackers from exploiting these vulnerabilities. Penetration testing often complements web application firewalls (WAF) in the context of web application security.
9. Discuss the importance of incident response in Cybersecurity.
Incident response is crucial for effectively managing and mitigating security incidents. It involves identifying, containing, investigating, and responding to security breaches or incidents promptly. A well-defined incident response plan ensures a swift and coordinated approach to minimize damage, recover systems, and prevent future incidents.
10. What are the essential components of a strong password policy?
A strong password policy includes requirements such as using complex passwords with a combination of uppercase and lowercase letters, numbers, and special characters. It also emphasizes regular password updates, prohibiting password sharing, and implementing multi-factor authentication for added security.
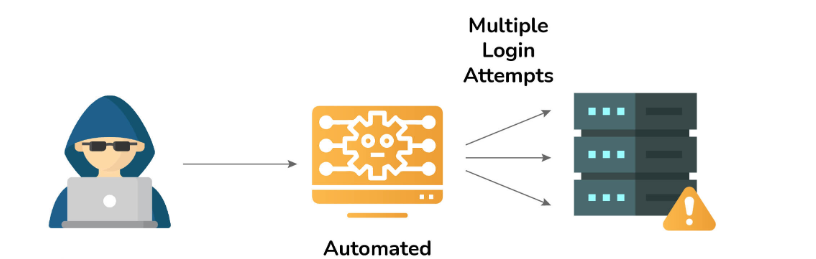
11. What do you mean by brute force in the context of Cyber Security?
A brute force attack is a cryptographic attack method employed by cybercriminals, which involves systematically attempting all possible combinations until the correct data is found. This technique is frequently utilized to acquire sensitive information such as passwords, login credentials, encryption keys, and PINs. Brute force attacks are relatively straightforward for hackers to execute, making them a common exploit in the realm of cybersecurity.
12. Explain the concept of malware and provide examples of different types.
Malware refers to malicious software designed to harm or exploit computer systems. Examples of different types of malware include viruses, worms, Trojans, ransomware, spyware, and adware. Each type has distinct characteristics and purposes, but they all pose a threat to system security.
13. How does two-factor authentication enhance security?
Two-factor authentication (2FA) adds an extra layer of security by requiring users to provide two forms of authentication to access a system or account. It typically combines something the user knows (e.g., a password) with something the user possesses (e.g., a unique code sent to a mobile device). This mitigates the risk of unauthorized access even if the password is compromised.
14. What is the role of a security audit in Cybersecurity?
A security audit is a systematic evaluation of an organization’s security measures to identify vulnerabilities, assess risks, and ensure compliance with security standards. It helps identify gaps in security controls, evaluate the effectiveness of security measures, and make recommendations for improvement.
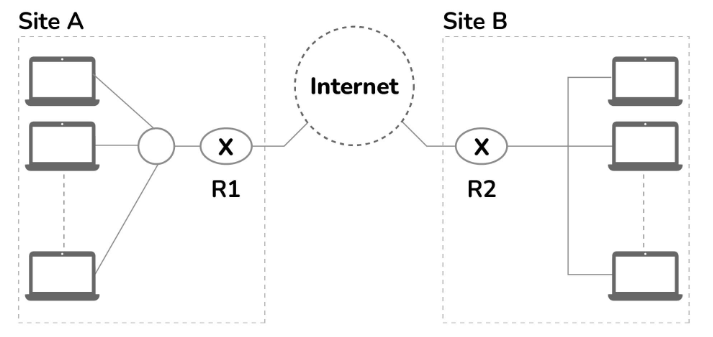
15. Differentiate between VPN and VLAN.
VLANs are utilized by companies to consolidate dispersed devices from multiple remote sites into a single broadcast domain. On the other hand, VPNs are employed to securely transmit data between two offices within the same organization or between offices of different companies. Additionally, individuals use VPNs for personal purposes.
A VLAN can be considered a subtype of VPN. VPN, short for Virtual Private Network, is a technology that establishes a virtual tunnel to ensure secure data transfer over the internet. While a VPN provides encryption and anonymization, making it a more advanced but costlier solution, a VLAN is primarily used to segment a network into logical sections for easier management, lacking the security features of a VPN.
16. Discuss the principles of least privilege and need-to-know in access control.
The principle of least privilege restricts user permissions to the minimum necessary level required to perform their tasks, reducing the potential for unauthorized access and limiting the damage that can be caused by compromised accounts. The principle of need-to-know restricts access to information only to individuals who require it based on their roles and responsibilities.
17. What is a DDoS attack, and how can it be mitigated?
A DDoS (Distributed Denial of Service) attack involves overwhelming a target system or network with a flood of malicious traffic from multiple sources, rendering it unavailable to legitimate users. Mitigation techniques include traffic filtering, rate limiting, and utilizing DDoS mitigation services or appliances to absorb and block malicious traffic.
18. Explain the concept of social engineering and its impact on security.
Social engineering is the psychological manipulation of individuals to deceive them into divulging sensitive information or performing actions that compromise security. It exploits human vulnerabilities rather than technical weaknesses. Social engineering techniques include phishing, pretexting, baiting, and tailgating.
19. What are the best practices for securing wireless networks?
Best practices for securing wireless networks include implementing strong encryption protocols like WPA2 or WPA3, disabling unnecessary network services, changing default passwords, enabling network segmentation, using strong and unique network passwords, and regularly updating firmware and security patches.
20. Describe the role of an Intrusion Detection System (IDS) in Cybersecurity.
An Intrusion Detection System (IDS) monitors network traffic or system activity for suspicious patterns or known attack signatures. It alerts administrators or takes automated actions to detect and respond to potential security incidents. IDS can be network-based (NIDS) or host-based (HIDS).
21. Discuss the importance of regular software patching in maintaining security.
Regular software patching is crucial for maintaining security as it helps address vulnerabilities and weaknesses discovered in software. Patching ensures that systems are up-to-date with the latest security fixes and reduces the risk of exploitation by known threats.
22. How can you ensure secure data transmission over a network?
Secure data transmission over a network can be ensured by using encryption protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL). These protocols encrypt data in transit, protecting it from unauthorized access or interception.
23. What is the purpose of penetration testing in Cybersecurity?
Penetration testing, also known as ethical hacking, is a method of assessing the security of a system by simulating real-world attacks. Its purpose is to identify vulnerabilities, assess the effectiveness of security controls, and provide recommendations for remediation.
24. Explain the concept of network segmentation and its benefits.
Network segmentation involves dividing a network into smaller, isolated segments to improve security and reduce the impact of a breach. It limits lateral movement within the network, reduces the attack surface, and enables granular access control based on business needs.
25. What are the key differences between symmetric and asymmetric encryption?
Symmetric encryption uses a single shared key for both encryption and decryption, making it faster but requiring a secure key exchange. Asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. It provides secure key exchange but is computationally more intensive.
26. What is the difference between a virus and a worm?
A virus requires a host file or program to attach itself to and requires user action to spread, while a worm is a standalone program that can spread itself across networks without user intervention.
27. Discuss the concept of zero-day vulnerabilities.
Zero-day vulnerabilities refer to security vulnerabilities that are unknown to software developers and have no available patch or fix. They are attractive to attackers as they can exploit them before they are discovered and patched.
28. What is the syntax for specifying a range of IP addresses in CIDR notation?
To specify a range of IP addresses in CIDR notation, you use the syntax <starting_IP_address>/<subnet_mask>. For example, 192.168.0.0/24 represents a range of IP addresses from 192.168.0.0 to 192.168.0.255.
29. What is the syntax for creating a regular expression to match an email address?
The syntax for creating a regular expression to match an email address is /^[\w-]+(.[\w-]+)*@([\w-]+.)+[a-zA-Z]{2,7}$/. This regex pattern ensures that the email address follows the standard format with the proper username, domain, and top-level domain.
30. What is the syntax for creating a strong password policy?
The syntax for creating a strong password policy typically involves setting requirements such as minimum password length, complexity rules (e.g., uppercase, lowercase, numbers, special characters), password expiration, and disallowing common passwords.
31. What is the syntax for writing a firewall rule to allow incoming SSH connections from a specific IP address?
The syntax for writing a firewall rule to allow incoming SSH connections from a specific IP address depends on the firewall software or platform being used. Generally, it involves specifying the source IP address and the port number (typically 22 for SSH) in the rule configuration.
32. What is the syntax for writing a command to perform a ping sweep on a range of IP addresses?
The syntax for performing a ping sweep on a range of IP addresses varies depending on the operating system. For example, in Windows, the syntax would be “for /L % I in (1,1,255) do ping -n 1 192.168.0.%i” to ping all IP addresses from 192.168.0.1 to 192.168.0.255.
33. What is the syntax for writing a command to list all running processes in Linux?
The syntax for listing all running processes in Linux is “ps aux”. This command displays detailed information about all processes running on the system, including their process IDs, memory usage, CPU utilization, and more.
34. What is the syntax for writing a command to check the integrity of a file using the SHA-256 hashing algorithm?
The syntax for checking the integrity of a file using the SHA-256 hashing algorithm is “sha256sum <filename>”. This command calculates the SHA-256 hash value of the specified file and compares it with the known hash value to verify its integrity.
35. What is the syntax for writing a command to perform a traceroute to a remote host?
The syntax for performing a traceroute to a remote host is “traceroute <hostname/IP>”. This command sends ICMP or UDP packets to the destination host with gradually increasing TTL (Time To Live) values, displaying the route taken and round-trip times for each hop.
36. What is the syntax for writing a command to list all open network connections in Windows?
The syntax for listing all open network connections in Windows is “netstat -ano”. This command provides information about active network connections, listening ports, associated processes, and their respective process IDs.
37. What is the syntax for writing a command to display the routing table in a Linux system?
The syntax for displaying the routing table in a Linux system is “ip route show” or “route -n”. These commands provide information about the network routes, including destination networks, gateway addresses, interface names, and metrics.
38. What is the role of encryption in data protection?
Encryption transforms data into an unreadable format using cryptographic algorithms, ensuring that only authorized individuals with encryption keys can access and understand the data. It plays a vital role in maintaining data confidentiality.
39. Explain the difference between symmetric and asymmetric encryption.
Symmetric encryption uses a single shared key for both encryption and decryption, while asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption.
40. Differences between symmetric and asymmetric encryption algorithms in cybersecurity
| Symmetric Encryption | Asymmetric Encryption |
|---|---|
| The same key is used for encryption and decryption | Different keys are used for encryption and decryption |
| Faster processing speed | Slower processing speed |
| Typically used for bulk data encryption | Used for secure key exchange and digital signatures |
| Requires secure key distribution | Eliminates the need for secure key distribution |
| Examples: AES, DES, 3DES | Examples: RSA, ECC, DSA |
41. Discuss the importance of regular data backups in Cybersecurity.
Regular data backups are crucial in Cybersecurity as they provide a means to recover data in the event of data loss due to hardware failure, ransomware attacks, or other incidents. They help ensure data availability and facilitate business continuity.
42. What is multi-factor authentication (MFA)?
Multi-factor authentication is a security mechanism that requires users to provide two or more different types of authentication factors, such as passwords, biometrics, smart cards, or one-time codes, to verify their identity.
43. What is the difference between penetration testing and vulnerability scanning?
Penetration testing involves actively testing systems, networks, or applications for vulnerabilities and attempting to exploit them, while vulnerability scanning focuses on identifying vulnerabilities through automated scans without exploiting them.
44. Discuss the concept of data loss prevention (DLP) in Cybersecurity.
Data loss prevention refers to the practices and technologies implemented to prevent the unauthorized or accidental transmission, storage, or disclosure of sensitive data. It aims to protect sensitive information and maintain regulatory compliance.
45. Differences between a firewall and an intrusion detection system (IDS)
| Firewall | Intrusion Detection System (IDS) |
|---|---|
| Acts as a barrier between internal and external networks, controlling incoming and outgoing traffic | Monitors network traffic and detects suspicious activities or unauthorized access |
| Filters network traffic based on predefined rules or policies | Analyzes network packets and events for potential security breaches |
| Works at the network and transport layers of the OSI model | Works at the network and application layers of the OSI model |
| Can block or allow traffic based on rules | Alerts administrators about potential security incidents |
46. What is the role of an intrusion detection system (IDS) in Cybersecurity?
An intrusion detection system monitors network or system activity, analyzing it for signs of potential security breaches or policy violations. It can generate alerts, notify administrators, or take automated actions in response to detected threats.
47. Explain the concept of access control in Cybersecurity.
Access control refers to the mechanisms and policies implemented to regulate and restrict user access to systems, networks, or data. It ensures that only authorized individuals can access the appropriate resources based on their roles and privileges.
48. What are the main objectives of incident response in Cybersecurity?
The main objectives of incident response are to minimize the impact of security incidents, contain the damage, investigate the root causes, restore systems and services, and learn from the incident to prevent similar future occurrences.
49. Discuss the importance of user awareness training in Cybersecurity.
User awareness training is essential in Cybersecurity as it educates users about potential risks, security best practices, and how to recognize and respond to threats such as phishing emails, social engineering attempts, or suspicious activities.
50. Differences between a virus and a worm in the context of cybersecurity threats
| Virus | Worm |
|---|---|
| Requires a host file or program to spread | Self-replicating and spreads without needing a host file or program |
| Often attaches itself to executable files or documents | Exploits vulnerabilities to propagate and spread across networks |
| Typically requires user interaction to execute | Spreads automatically without user interaction |
| Can modify or delete files on the infected system | Can consume network bandwidth and cause network congestion |
51. Explain the concept of a man-in-the-middle (MITM) attack.
A man-in-the-middle attack occurs when an attacker intercepts and alters the communication between two parties without their knowledge. The attacker can eavesdrop, modify data, or impersonate one or both parties, potentially compromising the integrity and confidentiality of the communication.
52. What is the principle of separation of duties in access control?
The principle of separation of duties requires that critical actions or functions be divided among multiple individuals to prevent a single person from having complete control or access. It helps reduce the risk of unauthorized activities or fraud.
53. Discuss the concept of identity and access management (IAM) in Cybersecurity.
Identity and access management is a framework of policies, processes, and technologies used to manage user identities, roles, and access rights within an organization. It ensures that the right individuals have the right access to the right resources at the right time.
54. What is a security incident response plan?
A security incident response plan outlines the predefined steps and procedures to be followed in the event of a security incident. It includes roles and responsibilities, communication protocols, incident escalation, containment strategies, and recovery steps.
55. Explain the concept of network monitoring and its importance in Cybersecurity.
Network monitoring involves the continuous monitoring and analysis of network traffic, devices, and systems to detect potential security incidents, performance issues, or policy violations. It helps identify suspicious activities, ensure network availability, and aid in incident response.
56. Differences between a Denial of Service (DoS) attack and a Distributed Denial of Service (DDoS) attack
| Denial of Service (DoS) Attack | Distributed Denial of Service (DDoS) Attack |
|---|---|
| Uses a single source or a few sources to flood a target with excessive traffic | Utilizes multiple sources to overwhelm the target with a massive amount of traffic |
| Aims to make a system or network unavailable to legitimate users | Targets the network infrastructure, services, or applications to disrupt their normal functioning |
| Can be mitigated by blocking the attacking source | Requires more complex mitigation techniques, such as traffic filtering or rate limiting |
| Often originates from a single compromised device or network | Involves multiple compromised devices forming a botnet to launch the attack |
57. Discuss the concept of encryption key management.
Encryption key management involves the secure generation, distribution, storage, rotation, and disposal of encryption keys. It ensures the confidentiality and integrity of encrypted data by properly managing the keys used for encryption and decryption.
58. What is a security information and event management (SIEM) system?
A security information and event management system is a centralized platform that collects, analyzes, and correlates security events and logs from various sources. It provides real-time visibility into security incidents, helps identify patterns or anomalies, and facilitates incident response.
59. Explain the concept of secure coding practices.
Secure coding practices involve following guidelines and best practices during software development to minimize security vulnerabilities. This includes input validation, secure authentication and authorization, error handling, secure data storage, and regular code reviews and testing.
60. Discuss the difference between vulnerability and risk in Cybersecurity.
Vulnerability refers to a weakness or flaw in a system or application that can be exploited by attackers. Risk, on the other hand, is the likelihood of a vulnerability being exploited and the potential impact or harm it can cause to an organization’s assets or operations.
61. What are the key components of a disaster recovery plan?
A disaster recovery plan typically includes a detailed inventory of critical systems and data, backup and recovery procedures, recovery time objectives (RTO) and recovery point objectives (RPO), a communication plan, and a testing and maintenance strategy.
62. Explain the concept of security by design.
Security by design is an approach where security measures and considerations are incorporated into the design and development of systems, applications, or products from the outset. It aims to proactively address security requirements and minimize vulnerabilities.
63. Differences between white hat hackers and black hat hackers
| White Hat Hackers | Black Hat Hackers |
|---|---|
| Ethical hackers who work to find vulnerabilities and improve security | Malicious hackers who exploit vulnerabilities for personal gain or harm |
| Authorized and work within legal boundaries | Engage in illegal activities and operate without authorization |
| Often employed by organizations to enhance cybersecurity | Operate independently or as part of criminal organizations |
| Obtain proper consent before performing any security testing | Conduct unauthorized penetration tests and malicious activities |
64. Discuss the concept of data classification and its role in data protection.
Data classification involves categorizing data based on its sensitivity, value, or regulatory requirements. It helps determine appropriate security controls, access levels, and handling procedures to ensure that data is protected based on its classification.
65. What are the differences between a black box test and a white box test?
In a black box test, the tester has no knowledge of the internal workings of the system being tested and focuses on its external behavior. In a white box test, the tester has full knowledge of the system’s internal structure, design, and code, allowing for more comprehensive testing.
66. Discuss the concept of security awareness training.
Security awareness training involves educating employees or users about security risks, threats, and best practices. It aims to raise awareness, promote responsible behavior, and empower individuals to make informed security decisions in their day-to-day activities.
67. What is the role of a security operations center (SOC)?
A security operations center is a centralized unit responsible for monitoring, analyzing, and responding to security incidents and threats. It employs a combination of people, processes, and technologies to ensure the ongoing security of an organization’s systems and data.
68. Differences between biometric authentication and traditional username-password authentication methods
| Biometric Authentication | Traditional Username-Password Authentication |
|---|---|
| Uses unique physiological or behavioral traits for identification | Relies on a combination of a username and password for authentication |
| Examples: Fingerprint, facial recognition, iris scan | Examples: User-selected passwords, passphrases |
| Difficult to replicate or spoof biometric traits | Susceptible to password cracking, brute-force attacks, or password reuse |
| Offers higher security and convenience in authentication | Requires users to remember and manage passwords |
69. Discuss the concept of incident response playbooks.
Incident response playbooks are pre-defined, documented procedures that outline step-by-step actions to be taken during a security incident. They provide guidance to incident response teams, ensuring a consistent and effective response to different types of incidents.
70. What is the principle of least privilege (PoLP) in access control?
The principle of least privilege states that users should be granted the minimum level of access necessary to perform their job functions. It helps reduce the risk of unauthorized access or privilege misuse and limits the potential impact of compromised accounts.
71. Explain the concept of security audits and their importance in Cybersecurity.
Security audits involve assessing and evaluating the effectiveness of an organization’s security controls, policies, and procedures. They help identify vulnerabilities, weaknesses, and non-compliance with security standards or regulations, allowing for remediation and continuous improvement.
72. Differences between phishing attacks and spear phishing attacks
| Phishing Attacks | Spear Phishing Attacks |
|---|---|
| Generic and mass-targeted email or message campaigns | Highly targeted attacks tailored to specific individuals or groups |
| Impersonates legitimate organizations or individuals to deceive victims | Personalizes the attack using information about the target |
| Typically involves a large number of potential victims | Focuses on a smaller group of carefully selected targets |
| Aims to obtain sensitive information, credentials, or financial details | May target specific individuals for espionage, fraud, or sabotage |
| Examples: “Nigerian Prince” scams, fake banking emails | Examples: CEO fraud, targeted malware attacks |
73. Discuss the concept of security incident classification and prioritization.
Security incident classification involves categorizing incidents based on their severity, impact, or potential harm to the organization. Prioritization determines the order in which incidents are addressed, focusing resources on those with the highest risk or impact.
74. What is the role of a security policy in Cybersecurity?
A security policy defines an organization’s guidelines, rules, and expectations regarding security practices, procedures, and behavior. It provides a framework for implementing and maintaining effective security controls and ensuring compliance with industry standards and regulations.
75. Explain the concept of data masking and its use in data privacy.
Data masking is a technique used to replace sensitive or confidential data with realistic but fictitious data. It allows organizations to use and share data for development, testing, or analytics purposes while protecting the privacy and confidentiality of the original data.
76. What is the role of a security incident response team?
A security incident response team is responsible for detecting, investigating, and responding to security incidents. They work to mitigate the impact of incidents, coordinate the response effort, and facilitate the recovery and restoration of affected systems and data.
77. Discuss the concept of network segmentation in Cybersecurity.
Network segmentation involves dividing a network into smaller, isolated segments to limit the lateral movement of threats and contains potential breaches. It helps enhance network security by isolating sensitive systems or data from other parts of the network.
78. What is the difference between authentication and authorization?
Authentication is the process of verifying the identity of a user or entity attempting to access a system or resource. Authorization, on the other hand, involves granting or denying access rights and privileges based on the authenticated user’s roles and permissions.
79. Explain the concept of incident escalation in Cybersecurity.
Incident escalation refers to the process of raising the severity or priority level of a security incident based on its impact, complexity, or potential risk. It ensures that incidents are appropriately prioritized and the necessary resources and expertise are allocated for their resolution.
80. Differences between symmetric and asymmetric key algorithms in secure communication protocols like SSL/TLS
| Symmetric Key Algorithms | Asymmetric Key Algorithms |
|---|---|
| Uses the same key for encryption and decryption | Utilizes different keys for encryption and decryption |
| Offers faster processing and is efficient for bulk data encryption | Slower processing due to complex mathematical operations |
| Examples: AES, 3DES | Examples: RSA, ECC, Diffie-Hellman |
| Requires secure key distribution to ensure confidentiality | Supports secure key exchange and digital signatures |
| Suitable for data confidentiality and integrity | Used for secure key establishment and authentication |
81. Discuss the concept of secure software development life cycle (SDLC) practices.
Secure software development life cycle practices involve integrating security measures throughout the software development process. This includes secure coding practices, threat modeling, code reviews, vulnerability testing, and secure deployment to mitigate potential security risks.
82. What are the common types of malware?
Common types of malware include viruses, worms, trojans, ransomware, spyware, adware, and rootkits. Each type of malware has its own characteristics and methods of infection or damage.
83. Explain the concept of risk assessment in Cybersecurity.
Risk assessment involves identifying, evaluating, and prioritizing potential risks and vulnerabilities to an organization’s systems, networks, or data. It helps determine the likelihood and potential impact of threats and assists in implementing appropriate risk mitigation measures.
84. Differences between data encryption and data obfuscation techniques
| Data Encryption | Data Obfuscation Techniques |
|---|---|
| Converts plaintext into ciphertext using cryptographic algorithms | Alters data representation or structure to make it less understandable |
| Requires a cryptographic key to encrypt and decrypt the data | Doesn’t necessarily involve a specific key or decryption process |
| Provides strong confidentiality and protection against unauthorized access | Focuses on hiding or disguising data without providing strong security |
| Examples: AES encryption, RSA encryption | Examples: Data masking, tokenization, data shuffling |
85. Discuss the concept of security controls in Cybersecurity.
Security controls are measures or safeguards implemented to protect systems, networks, or data from security threats. They can be technical controls (firewalls, antivirus software), physical controls (access control systems), or administrative controls (policies, procedures).
86. What is the difference between a vulnerability assessment and a penetration test?
A vulnerability assessment involves scanning and identifying potential vulnerabilities in systems, networks, or applications. A penetration test goes a step further by actively exploiting identified vulnerabilities to assess the impact and potential for unauthorized access or compromise.
87. Explain the concept of security incident reporting and communication.
Security incident reporting and communication involve timely and accurate reporting of security incidents to the appropriate stakeholders, such as incident response teams, management, and regulatory bodies. Effective communication helps ensure a coordinated response and facilitates decision-making.
88. What is the role of security awareness training for employees?
Security awareness training for employees aims to educate them about potential security risks, threats, and best practices. It helps foster a security-conscious culture, empowers employees to recognize and report security incidents, and reduces the risk of human-related security breaches.
89. Discuss the concept of secure remote access in Cybersecurity.
Secure remote access refers to providing users with secure and controlled access to an organization’s systems, networks, or resources from remote locations. It involves implementing authentication mechanisms, encryption protocols, and secure VPN connections to protect against unauthorized access.
90. Differences between a vulnerability and an exploit in the field of cybersecurity
| Vulnerability | Exploit |
|---|---|
| Weaknesses or flaws in software, hardware, or systems | Software code or technique used to take advantage of a vulnerability |
| May exist due to design, implementation, or configuration errors | Takes advantage of vulnerabilities to gain unauthorized access or control |
| Represents a potential security risk or entry point for attackers | Actively leverages vulnerabilities to compromise a system or network |
91. Explain the concept of security information sharing and collaboration.
Security information sharing and collaboration involve the exchange of threat intelligence, incident data, and best practices among organizations, industry groups, and government entities. It helps enhance collective defense, improve incident response capabilities, and stay updated on emerging threats.
92. What is the role of security assessments and audits in Cybersecurity?
Security assessments and audits involve evaluating an organization’s security controls, policies, and procedures to identify vulnerabilities, weaknesses, or non-compliance. They provide valuable insights to improve security posture, ensure regulatory compliance, and address potential gaps.
93. Discuss the concept of secure email communication.
Secure email communication involves encrypting email messages to protect their confidentiality and integrity during transmission. It utilizes encryption protocols such as S/MIME or PGP to ensure that only the intended recipients can access and read the email content.
94. What are the key components of a strong password policy?
Key components of a strong password policy include password complexity requirements, regular password expiration, multi-factor authentication, password hashing or encryption, and user education on creating and maintaining secure passwords.
95. Explain the concept of security incident containment and eradication.
Security incident containment and eradication involve isolating affected systems or networks, mitigating the impact of an incident, and removing the root cause of the security breach. It aims to restore normal operations and prevent further unauthorized access or damage.
96. What is the difference between a virus and a worm?
A virus is a malicious program that requires user interaction to spread, while a worm is a self-replicating program that can spread across networks without user intervention.
97. What form of cookie might be used in a spyware attack?
Tracking cookies are commonly used in spyware attacks. They collect user data without consent or knowledge to gather sensitive information.
98. What are polymorphic viruses?
Polymorphic viruses are malicious software that can change their code or signature with each infection, making them harder to detect by antivirus software.
99. What is active reconnaissance?
Active reconnaissance refers to the process of actively probing and scanning a target network or system to gather information and identify vulnerabilities before launching an attack or assessing security.
100. What are the benefits of Cyber Security?
The following are some of the advantages of putting cybersecurity in place and keeping it up to date:
- Businesses are protected from cyberattacks and data breaches.
- Both data and network security are safeguarded.
- Unauthorized user access is kept to a minimum.
- There is a quicker recovery time after a breach.
- Protection for end-users and endpoint devices.
- Regulatory compliance.
This collection of Top 100 Cybersecurity Interview Questions and Answers can be a valuable resource for job seekers preparing for Cybersecurity Technical Interview Questions in the field. By following reliable sources such as freshersnow.com, individuals can stay informed about the latest developments in Cybersecurity and enhance their knowledge to excel in the Cybersecurity Interview Questions and Answers process.



