
This article provides a list of 100 Kubernetes interview questions and answers, covering a range of topics including Kubernetes interview questions for beginners and experienced developers. The purpose of these questions is to equip candidates with the necessary knowledge and skills to excel in Kubernetes interviews.
By going through these comprehensive questions, you can build confidence in your Kubernetes knowledge and increase your chances of success in the interview process.
★★ Latest Technical Interview Questions ★★
Top 100 Kubernetes Interview Questions and Answers
1. What is Kubernetes and how does it differ from other container orchestration tools?
Kubernetes is an open-source container orchestration tool that automates container deployment, scaling, and management. It differs from other container orchestration tools in its ability to manage containerized applications across multiple hosts and clusters, its extensive API and CLI interfaces, and its support for a wide range of container runtimes
2. What are the benefits of using Kubernetes in container deployment and management?
Some benefits of using Kubernetes in container deployment and management include simplified application deployment, improved resource utilization, easier scaling and load balancing, automated health monitoring and recovery, and seamless integration with other tools and services.
3. What is the syntax for creating a Kubernetes deployment?
The syntax for creating a Kubernetes deployment is
"kubectl create deployment [deployment-name] --image=[image-name]".
4. What are the different types of services in Kubernetes?
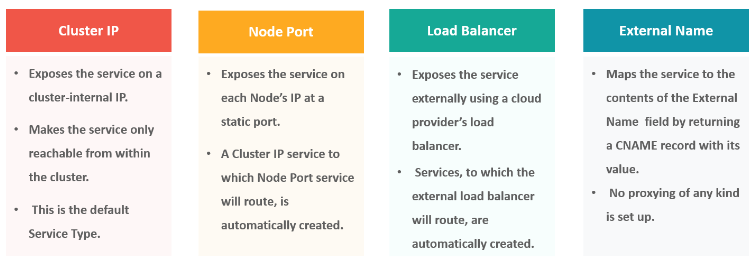
5. What are the different Kubernetes components and their roles in the cluster?
| Component | Role |
|---|---|
| API Server | Acts as the cluster’s control plane and exposes the Kubernetes API. |
| etcd | A distributed key-value store that stores the configuration data and cluster state. |
| Controller Manager | A component that runs various control loops that regulate the state of the cluster. |
| Scheduler | Assigns a node to a newly created pod based on resource availability and other constraints. |
| kubelet | An agent that runs on each node in the cluster and is responsible for managing the node’s pods and containers. |
| kube-proxy | A network proxy that runs on each node and is responsible for load-balancing network traffic between services. |
| Container Runtime | The software is responsible for running containers, such as Docker, contained, or CRI-O. |
| Add-ons | Optional components that provide additional features, such as DNS resolution and dashboard UI. |
6. What is the syntax for creating a Kubernetes service?
The syntax for creating a Kubernetes service is
"kubectl create service [service-type] [service-name] --tcp=[port-number]:[target-port-number]".
7. What do you understand by a node in Kubernetes?
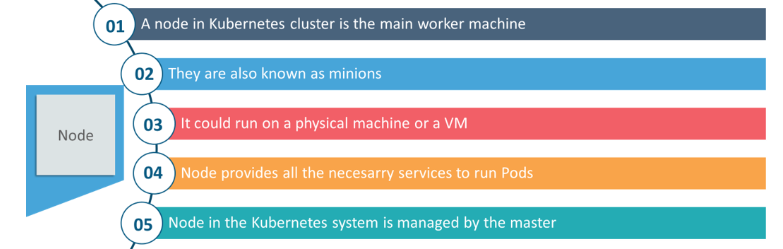
8. How to turn the service defined below in the spec into an external one?
spec: selector: app: some-app ports: - protocol: UDP port: 8080 targetPort: 8080>
9. What do you know about clusters in Kubernetes?
The core concept of Kubernetes revolves around enforcing the desired state management. This means that the cluster services can be provided with a specific configuration, and it becomes the responsibility of the cluster services to execute that configuration in the infrastructure.
10. What is the syntax for scaling a Kubernetes deployment?
The syntax for scaling a Kubernetes deployment is
"kubectl scale deployment [deployment-name] --replicas=[number-of-replicas]"
11. What are the best security measures that you can take while using Kubernetes?
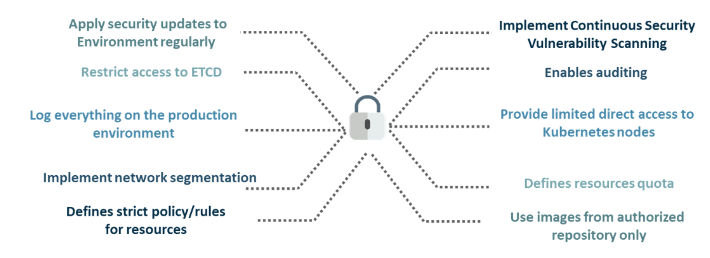
12. What is the difference between a Kubernetes persistent volume and a persistent volume claim?
| Topic | Kubernetes Persistent Volume | Kubernetes Persistent Volume Claim |
|---|---|---|
| Use case | Provide persistent storage to pods | Request and use persistent storage |
| Resource types | Storage backend, such as a network-attached storage | Request for a specific amount of storage |
| Access modes | ReadWriteOnce, ReadOnlyMany, ReadWriteMany | Requested by a pod with a specific access mode |
| Example | Store user uploads to a file system | Request persistent storage for a database |
13. What is a Kubernetes service and how does it work?
A Kubernetes service is an abstraction layer that provides a stable IP address and DNS name for a set of pods. Services allow for easy discovery and access to pods and can be used to define network policies and load-balancing rules.
14. What are the features of Kubernetes?
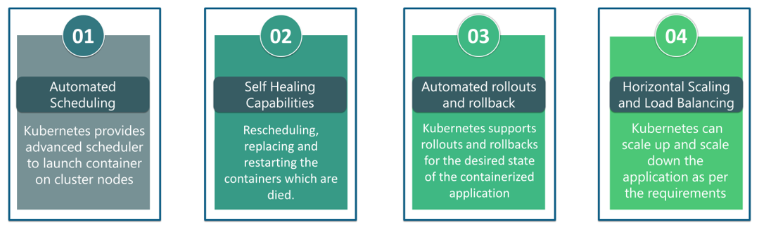
15. How do you manage Kubernetes configurations using ConfigMaps and Secrets?
Kubernetes ConfigMaps and Secrets are used to manage configuration data and sensitive information such as API keys and passwords, respectively. They allow for easy management and deployment of application configuration data without hardcoding it in the application code or Docker image.
16. What is the syntax for creating a Kubernetes ingress?
The syntax for creating a Kubernetes ingress is
"kubectl create ingress [ingress-name] --rule=[host-name]=[service-name]:[port-number]".
17. How do you perform rolling updates and rollbacks in Kubernetes?
Rolling updates and rollbacks in Kubernetes can be performed using the Kubectl rollout command. This allows for seamless updates of applications without downtime and easy rollback in case of issues.
18. What is the syntax for creating a Kubernetes ConfigMap?
The syntax for creating a Kubernetes ConfigMap is
"kubectl create configmap [configmap-name] --from-literal=[key]=[value]"
19. What are Kubernetes labels and selectors and how are they used to manage resources?
Kubernetes labels and selectors are used to attach metadata to Kubernetes objects such as pods, services, and deployments, and to select objects based on that metadata. They are used to manage resources and enable easy grouping and filtering of Kubernetes objects.
20. How do you set up and use Kubernetes ingress to expose services to the internet?
Kubernetes ingress is a Kubernetes API object used to expose HTTP and HTTPS routes from outside the cluster to services within the cluster. It provides a centralized and flexible way to manage external access to Kubernetes services.
21. What is the syntax for creating a Kubernetes Secret?
The syntax for creating a Kubernetes Secret is
"kubectl create secret [secret-type] [secret-name] --from-literal=[key]=[value]"
22. How do you use Kubernetes storage volumes to persist data in containers?
Kubernetes storage volumes allow for persistent storage of data in containers, even when containers are deleted or recreated. Kubernetes supports various types of storage volumes, including local storage, network-attached storage, and cloud-based storage.
23. What is a Kubernetes stateful set and how is it different from a deployment?
A Kubernetes StatefulSet is a controller used to manage stateful applications, such as databases or key-value stores. It provides guarantees around the ordering and uniqueness of pod creation and deletion and allows for easy scaling and rolling updates of stateful applications.
24. What is the difference between a Kubernetes operator and a controller?
| Topic | Kubernetes Operator | Kubernetes Controller |
|---|---|---|
| Use case | Automate complex tasks | Manage a specific resource |
| Resource Type | Custom resource types | Kubernetes core resources |
| Deployment | Deploy and manage applications | Deploy and manage resources |
| Example | Manage a database cluster | Manage a load balancer |
25. What is the syntax for creating a Kubernetes StatefulSet?
The syntax for creating a Kubernetes StatefulSet is
"kubectl create statefulset [statefulset-name] --image=[image-name]"
26. How do you monitor and troubleshoot Kubernetes clusters using metrics and logs?
You can use various tools like Prometheus, Grafana, and ELK stack to collect and analyze metrics and logs. These tools provide insights into the health and performance of the Kubernetes cluster and can help you identify and troubleshoot issues.
27. What is Kubernetes auto-scaling and how does it work?
Kubernetes auto-scaling is a feature that automatically adjusts the number of replicas of a deployment or a replica set based on resource utilization metrics like CPU and memory usage. It works by using horizontal pod auto-scalers (HPA) that monitor the resource utilization of pods and adjust the number of replicas accordingly.
28. What is the syntax for creating a Kubernetes CronJob?
The syntax for creating a Kubernetes CronJob is
"kubectl create cronjob [cronjob-name] --image=[image-name] --schedule=[cron-expression] -- [command]".
29. What are Kubernetes taints and tolerations and how are they used to schedule pods?
Kubernetes taints and tolerations are used to control which nodes can run specific pods. Taints are applied to nodes to indicate that they do not accept pods that do not tolerate taints. Tolerations are applied to pods to indicate that they can tolerate the taints and can be scheduled on the nodes with those taints.
30. How do you manage Kubernetes resources using quotas and limits?
You can use Kubernetes resource quotas to limit the number of resources that can be used by a namespace or a user in a cluster. Resource limits can be set for CPU, memory, and other resources to ensure that resources are used efficiently and fairly across the cluster.
31. What is the syntax for setting resource limits for a Kubernetes pod?
The syntax for setting resource limits for a Kubernetes pod is
"kubectl set resources [pod-name] [container-name] --limits=[resource-type]=[value]"
32. How do you deploy and manage Kubernetes applications using Helm charts?
Helm is a package manager for Kubernetes that allows you to define, install, and upgrade complex applications using charts. Charts are templates that define the structure of an application, including its dependencies, configurations, and services.
33. How does a Kubernetes job differ from a cronjob?
| Topic | Kubernetes Job | Kubernetes CronJob |
|---|---|---|
| Use case | Run a job to completion | Run a job on a schedule |
| Pod behavior | Creates pods until the job completes | Creates pods on a schedule |
| Pod lifecycle | Deletes pods after the job complete | Deletes pods after the job completes |
| Example | Backup a database once a day | Run a cleanup job every hour |
34. How do you secure a Kubernetes cluster using RBAC, TLS, and other security measures?
You can use role-based access control (RBAC) to control access to Kubernetes resources and implement Transport Layer Security (TLS) to secure communication between Kubernetes components. Other security measures like network policies and container image scanning can also be used to enhance the security of a Kubernetes cluster.
35. What are Kubernetes operators and how are they used to automate complex applications?
Kubernetes operators are custom controllers that extend Kubernetes functionality to automate complex applications. Operators use custom resource definitions (CRDs) to define and manage Kubernetes resources which can be used to automate tasks like backups, upgrades, and scaling.
36. What is the syntax for creating a Kubernetes Job?
The syntax for creating a Kubernetes Job is
"kubectl create job [job-name] --image=[image-name] -- [command]".
37. How do you use Kubernetes Jobs and CronJobs to run batch processes and scheduled tasks?
Kubernetes Jobs and CronJobs are used to run batch processes and scheduled tasks in a Kubernetes cluster. Jobs are used for one-time batch processes, while CronJobs are used for recurring scheduled tasks.
38. How do you integrate Kubernetes with other container orchestration tools like Docker Swarm and Mesos?
Kubernetes can be integrated with other container orchestration tools like Docker Swarm and Mesos using tools like Kompose and Kubernetes Universal Declarative Operator (KUDO). These tools allow you to convert Docker Compose files to Kubernetes manifests and automate tasks like application deployments and scaling.
39. What is a Kubernetes custom resource definition and how is it used to extend Kubernetes functionality?
A Kubernetes custom resource definition (CRD) is used to extend Kubernetes functionality by defining custom resources that can be used to manage complex applications. CRDs allow you to define and manage custom resources using Kubernetes API and can be used to automate tasks like backups, upgrades, and scaling.
40. How do you use Kubernetes rolling deployments to minimize downtime and maintain service availability?
Kubernetes rolling deployments allow you to update an application without downtime by gradually replacing old pods with new ones. This ensures that the application remains available during the update and minimizes downtime.
41. What is the difference between a Kubernetes secret and a config map?
| Topic | Kubernetes Secret | Kubernetes ConfigMap |
|---|---|---|
| Use case | Store sensitive information | Store configuration information |
| Data format | Encrypted data | Plain text data |
| Data type | Generic data types | Key-value pairs |
| Mounting | Can mount as files or environment variables | Can mount as files or environment variables |
42. How do you use Kubernetes liveness and readiness probes to ensure application health and availability?
- Kubernetes liveness and readiness probes are used to ensure that applications running in a container are healthy and ready to receive traffic.
- Liveness probes check if the container is still alive and responsive while readiness probes check if the container is ready to receive traffic.
- If a container fails a liveness probe, Kubernetes will automatically restart the container. If a container fails a readiness probe, Kubernetes will stop sending traffic to that container until it passes the probe.
43. What is the difference between a Kubernetes daemonset and a deployment?
- A Kubernetes deployment is used to manage the creation, scaling, and updating of replicas of a pod.
- A Kubernetes daemonset is used to ensure that all or some nodes in a cluster run a copy of a pod.
- Deployments are typically used for stateless applications that can scale horizontally, while daemonsets are used for stateful applications that require a unique instance on each node.
44. How do you use Kubernetes configmaps to configure applications and microservices?
- Kubernetes configmaps are used to store configuration data as key-value pairs and are used to decouple configuration from container images.
- Configmaps can be mounted as volumes in a pod or exposed as environment variables to containers in the pod.
- To use a configmap, you can create a configmap object and reference it in the pod specification.
45. What is the difference between Kubernetes node affinity and anti-affinity?
| Topic | Kubernetes Node Affinity | Kubernetes Node Anti-Affinity |
|---|---|---|
| Use case | Ensuring pods run on specific nodes | Avoiding scheduling pods on specific nodes |
| Node selection | Based on labels or custom rules | Based on labels or custom rules |
| Example | Run a pod on a node with specific hardware | Avoid running multiple pods on the same node |
46. How do you use Kubernetes node affinity and anti-affinity to schedule pods on specific nodes?
- Kubernetes node affinity and anti-affinity are used to schedule pods on specific nodes based on node labels or other node metadata.
- Node affinity is used to specify rules for scheduling pods on nodes that match certain labels or other attributes.
- Node anti-affinity is used to specify rules for avoiding scheduling pods on nodes that match certain labels or other attributes.
47. What is the role of Kubernetes kubelet in managing containers and nodes?
- The Kubernetes kubelet is responsible for managing the state of individual nodes in a cluster.
- The kubelet is responsible for starting and stopping containers, managing container storage, and monitoring container health.
- It communicates with the Kubernetes API server to receive instructions on which pods to run and how to manage them.
48. How do you use Kubernetes network policies to control network traffic between pods?
- Kubernetes network policies are used to control network traffic between pods based on rules defined in policy objects.
- Network policies can be used to allow or deny traffic based on pod labels, namespace, IP addresses, and other attributes.
- To use network policies, you need to install a network plugin that supports the Kubernetes network policy API.
49. What is the difference between Kubernetes quotas and limits?
| Topic | Kubernetes Quotas | Kubernetes Limits |
|---|---|---|
| Use case | Limits resource usage | Sets resource limits |
| Enforcement | Enforced at namespace level | Enforced at pod level |
| Types | Compute, memory, storage | Compute, memory, storage |
| Usage | Can set quotas on number of pods or services | Can set limits on CPU or memory usage |
50. How should TLS be configured with Ingress?
spec: tls: - hosts: - some_app.com secretName: someapp-secret-tls
51. How do you manage Kubernetes secrets securely using encryption and decryption techniques?
- Kubernetes secrets are used to store sensitive information such as passwords and keys as key-value pairs.
- Secrets are encrypted at rest and can only be accessed by authorized users or services.
- To manage secrets securely, you can encrypt and decrypt secrets using encryption keys stored in a Kubernetes secret or an external secret management service.
52. What are Kubernetes network plugins and how are they used to provide network connectivity to pods?
- Kubernetes network plugins are used to provide network connectivity to pods running in a cluster.
- Network plugins implement the Kubernetes CNI (Container Network Interface) specification and are responsible for setting up and managing networking for containers.
- Examples of Kubernetes network plugins include Calico, Flannel, and Weave Net.
53. How do you use Kubernetes Helm to package, deploy, and manage applications on a cluster?
- Kubernetes Helm is a package manager for Kubernetes that allows you to package, deploy, and manage applications and services on a cluster.
- Helm uses charts to define the structure of an application, including its dependencies, configuration, and deployment strategies.
- You can use Helm to install, upgrade, and uninstall applications and services on a Kubernetes cluster.
54. What are Kubernetes admission controllers and how are they used to enforce policies and security measures?
Kubernetes admission controllers are a set of plug-ins that are used to enforce policies and security measures on resources as they are created or modified in a cluster. Admission controllers can be used to validate and mutate requests to the Kubernetes API server, and they can be used to enforce custom policies or security measures, such as requiring pod labels or preventing the creation of pods that use privileged containers.
55. How do you use Kubernetes State Metrics to monitor the health and performance of a cluster?
Kubernetes State Metrics is a tool that collects and exposes metrics about the state of Kubernetes resources, such as pods, nodes, and deployments. These metrics can be used to monitor the health and performance of a cluster and to detect and diagnose issues. State Metrics provides a set of Prometheus metrics endpoints that can be scraped by a monitoring system, such as Prometheus or Grafana.
56. What is the difference between a Kubernetes namespace and a label?
A Kubernetes namespace is a virtual cluster that is used to partition a physical cluster into multiple logical clusters. Namespaces are used to isolate resources, such as pods and services, and to provide a scope for access control and resource quotas. In contrast, a label is a key-value pair that is used to attach metadata to resources, such as pods and services, and to group resources based on common attributes
57. What is the difference between a Kubernetes deployment and a stateful set?
| Topic | Kubernetes Deployment | StatefulSet |
|---|---|---|
| Use case | Stateless applications | Stateful applications |
| Scaling | Can scale horizontally | Can scale horizontally or vertically |
| Ordering | No ordering guarantee | Deploys in a sequential order |
| Pod naming | Uses random names | Uses ordered names |
| Persistence | No persistence | Can persist data across pod restarts |
58. How does a Kubernetes service differ from an ingress?
| Topic | Kubernetes Service | Ingress |
|---|---|---|
| Use case | Internal networking | Exposes services to outside |
| Traffic routing | Uses labels to route | Uses rules to route |
| Load balancing | Can balance traffic | Can balance traffic |
| SSL termination | No SSL termination | Can terminate SSL |
59. How does a Kubernetes daemonset differ from a replica set?
TopicKubernetes DaemonSetKubernetes ReplicaSetUse case run a copy of a pod on every nodeEnsure a specific number of replicas of a podPod placement place on every nodeCan place on specific nodesScalingScales with nodesScales with number of replicasPod deletionDeletes pods when a node is removedDeletes pods when no longer needed
60. How does Kubernetes horizontal pod autoscaling differ from vertical pod autoscaling?
| Topic | Kubernetes Horizontal Pod Autoscaling | Kubernetes Vertical Pod Autoscaling |
|---|---|---|
| Use case | Automatically scale pods based on CPU or memory usage | Automatically adjust resource limits based on usage |
| Scaling | Scales number of replicas | Adjusts resource limits |
61. What does the node status contain in Kubernetes?
In Kubernetes, the main components of a node status are Address, Condition, Capacity, and Info.
62. What process is used to run on the Kubernetes Master Node?
The Kube-api server process runs on the Kubernetes Master Node. It is used to scale the deployment of more instances.
63. What are the different types of controller managers?
- Endpoints controller
- Service accounts controller
- Namespace controller
- Node controller
- Replication controller
- Token controller
64. What is the biggest disadvantage of Kubernetes?
- Security is the biggest issue with Kubernetes. It is not very secure.
- Kubernetes dashboard is not very user-friendly.
- Kubernetes is very complex to use. That’s why it can reduce productivity.
- Kubernetes is costlier than its alternatives.
65. What are the various services available in Kubernetes?
- Cluster IP service
- Load Balancer service
- Node Port service
- External Name Creation service etc.
66. What are some examples of recommended security measures for Kubernetes?
- Support for auditing
- Restriction of etc access
- Regular security updates to the environment
- Network segmentation
- Definition of strict resource policies
- Continuous scanning for security vulnerabilities
- Using images from authorized repositories etc.
67. What do you understand by PVC? What is its full form?
PVC stands for Persistent Volume Claim. It is a Kubernetes resource that allows a Pod to request a specific amount of storage and use it as a volume.
68. What do you understand by Sematext Docker Agent?
Sematext Docker Agent is a monitoring and log management solution for Docker environments. It collects and aggregates logs, metrics, and events from Docker containers and the host operating system, providing insights and alerts for troubleshooting and performance optimization.
69. What is a sidecar container, and what is its use?
A sidecar container is a secondary container that runs alongside the main container in a Pod. It is used to provide additional functionality, such as logging, monitoring, or network proxying, without modifying the main container.
70. Explain Daemon sets.
DaemonSets are a type of Kubernetes controller that ensures a set of Pods are running on all or a subset of nodes in a cluster. They are typically used for running system-level daemons, such as monitoring agents or network proxies.
71. What are the different types of pods in Kubernetes?
In Kubernetes, there are two types of pods: single-container pods and multi-container pods. Single-container pods contain only one container, while multi-container pods contain multiple containers that share the same network namespace and can communicate with each other.
72. What is a pod and what does it do?
A pod is the smallest deployable unit in Kubernetes. It consists of one or more containers that share the same network namespace and can communicate with each other using localhost. Pods provide an abstraction layer for managing containers, allowing them to be easily scaled, replicated, and managed.
73. What do you understand by OpenShift in Kubernetes
OpenShift is a Kubernetes-based container platform developed by Red Hat. It provides a complete solution for deploying and managing containerized applications, including tools for building, deploying, and scaling applications, as well as integrated monitoring and security features.
74. What is ETCD in Kubernetes?
ETCD is a distributed key-value store that is used by Kubernetes to store cluster configuration and state information. It provides a highly available and consistent data store that can be accessed by all components of a Kubernetes cluster.
75. What do you understand by K8s in Kubernetes?
K8s is a shorthand term for Kubernetes. The “8” in K8s represents the eight letters between the “K” and “s” in “Kubernetes”. It is commonly used as an abbreviation in the Kubernetes community.
76. Why do we need Container orchestration in Kubernetes?
Container orchestration is necessary for Kubernetes to manage the deployment, scaling, and maintenance of containerized applications across a cluster of nodes. It automates many of the tasks involved in deploying and managing containers, such as load balancing, scaling, and self-healing.
77. Explain Stateful sets in Kubernetes.
StatefulSets are a type of Kubernetes controller that manages the deployment of stateful applications, such as databases or other systems that require persistent storage. They provide guarantees around ordering and uniqueness of Pods and can ensure that data is preserved even if a Pod fails or is rescheduled.
78. What is kubectl?
kubectl is the command-line tool used for managing Kubernetes clusters. It allows administrators and developers to interact with Kubernetes resources, such as Pods, Services, and Deployments, using a simple and intuitive command-line interface.
79. What is Heapster?
Heapster is a deprecated Kubernetes component that was used for collecting and aggregating cluster-wide performance metrics. It has been replaced by the Kubernetes Metrics Server, which provides a more efficient and scalable solution for monitoring resource utilization in Kubernetes clusters.
80. What is a Kubernetes Pod Disruption Budget, and how does it manage availability during upgrades?
A Kubernetes Pod Disruption Budget (PDB) is a resource that ensures the availability of a certain number of pods during upgrades or maintenance. It ensures that not all pods are terminated at once and can be used to define how many pods need to be available for a certain workload.
81. What is a Kubernetes Horizontal Pod Autoscaler, and how does it manage container scaling?
A Kubernetes Horizontal Pod Autoscaler (HPA) is a resource that automatically scales the number of pods in a deployment based on metrics such as CPU usage or custom metrics. It can be used to ensure that the workload can handle an increase in traffic.
82. How does Kubernetes handle container security, and what is a Security Context?
Kubernetes handles container security by using Security Contexts, which are used to define the security settings for a container, such as a user and group IDs, SELinux context, and capabilities. It can also be used to define network policies and configure pod-level security policies.
83. What is a Kubernetes Label, and how does it help manage resource categorization?
A Kubernetes Label is a key-value pair that is used to categorize resources, such as pods, services, and deployments. Labels can be used to group resources based on their functionality, location, or any other attribute that is relevant to the cluster.
84. What is a Kubernetes Annotation, and how does it help manage resource metadata?
A Kubernetes Annotation is a key-value pair that is used to attach metadata to Kubernetes resources. Annotations can be used to provide additional information about the resource, such as who created it or when it was last updated.
85. What is a Kubernetes namespace, and how does it enable resource isolation?
A Kubernetes namespace is a logical partitioning of a cluster and enables resource isolation and management for different teams or applications. It provides scope for naming and access control and prevents naming conflicts and resource collisions.
86. How does Kubernetes handle container upgrades, and what is a Rolling Update?
Kubernetes handles container upgrades using Rolling Updates, which are used to update deployment to a new version of the application without causing downtime. It can be used to gradually update the deployment by replacing old pods with new ones until all pods are updated.
87. What is a Kubernetes Cluster Autoscaler, and how does it manage cluster scaling?
A Kubernetes Cluster Autoscaler is a resource that automatically scales the number of nodes in a cluster based on the demand for resources. It can be used to ensure that the cluster can handle an increase in traffic and reduce costs during periods of low demand.
88. What is a Kubernetes Topology Spread Constraint, and how does it manage resource placement?
A Kubernetes Topology Spread Constraint is a resource that is used to manage resource placement in a cluster. It can be used to ensure that pods are spread across different nodes or different failure domains, to improve availability and reduce the impact of node failures.
89. What is a Kubernetes Priority Class, and how does it manage resource prioritization?
A Kubernetes Priority Class is a resource that is used to manage resource prioritization in a cluster. It can be used to prioritize critical workloads over less important ones, to ensure that the most important workloads have access to the resources they need.
90. How does Kubernetes handle container readiness checks, and what is a Readiness Probe?
Kubernetes handles container readiness checks using Readiness Probes, which are used to determine whether a container is ready to receive traffic. It can be used to delay traffic to a container until it has fully initialized or started up.
91. What is a Kubernetes Affinity Rule, and how does it manage resource scheduling?
A Kubernetes Affinity Rule is a resource that is used to manage resource scheduling in a cluster. It can be used to ensure that pods are scheduled on nodes that meet certain requirements, such as having specific labels or being located in a certain zone.
92. What are the advantages of Kubernetes?
Kubernetes is open-source and free
It is highly scalable and runs on any operating system
It provides more concepts and is more powerful than Docker swarm
It provides a scheduler, auto-scaling, rolling upgrades, and health checks
It has a flat network space and customized functionalities
93. What are the disadvantages of Kubernetes?
The installation process and configuration is highly difficult
It is not easy to manage the services
It takes a lot of time to run and compile
It can be overkill for simple application
94. What is NodePort?
The NodePort service is the most fundamental way to get external traffic directly to your service. It opens a specific port on all Nodes and forwards any traffic sent to this port to the service.
95. What is the LoadBalancer in Kubernetes?
The LoadBalancer service is used to expose services to the internet. A Network load balancer, for example, creates a single IP address that forwards all traffic to your service.
96. What is ClusterIP?
The ClusterIP is the default Kubernetes service that provides service inside a cluster (with no external access) that other apps inside your cluster can access.
97. What is an Operator?
As an extension to K8, the operator provides the capability of managing applications and their components using custom resources. Operators generally comply with all the principles relating to Kubernetes, especially those relating to the control loops.
98. What is the purpose of operators?
As compared to stateless applications, achieving desired status changes and upgrades are handled the same way for every replica, managing Kubernetes applications is more challenging.
99. What is etcd?
Kubernetes uses etcd as a distributed key-value store for all of its data, including metadata and configuration data, and allows nodes in Kubernetes clusters to read and write data
100. What is the Ingress network, and how does it work?
Ingress is an object that allows users to access your Kubernetes services from outside the Kubernetes cluster. Users can configure the access by creating rules that define which inbound connections reach which services.
By mastering the Top 100 Kubernetes interview questions and answers, you will gain the knowledge necessary to perform well in your Kubernetes technical interviews and increase your chances of securing your desired job. You can further enhance your understanding by following us at freshersnow.com.



