
Microservices Interview Questions and Answers: Microservices entail breaking down complex applications into smaller, independent services for increased agility and scalability. Each microservice focuses on a specific function, enabling independent development, deployment, and scaling. This approach enhances software efficiency, empowering organizations to deliver robust solutions. This article features a comprehensive compilation of the Top 50 Microservices Interview Questions and Answers, encompassing various aspects of the Latest Microservices Interview Questions. It serves as a valuable resource for individuals seeking in-depth knowledge of Microservices Technical Interview Questions.
Microservices Interview Questions for Freshers
This list presents the Top 50 Microservices Interview Questions and Answers, beneficial for enhancing understanding and excelling in Microservices interviews, especially for Freshers. Microservices are known for their reliability, security, and scalability, making them ideal for enterprise-level applications.
Top 50 Microservices Interview Questions and Answers
1. What are microservices and how do they differ from monolithic architectures?
Microservices are a software architecture approach where an application is divided into a collection of small, loosely coupled services that can be developed, deployed, and scaled independently. Unlike monolithic architectures, which have a single large codebase, microservices promote modularity and allow each service to have its own codebase and technology stack.
2. What are the main benefits of using microservices?
The main benefits of using microservices include:
- Scalability: Services can be scaled independently based on demand.
- Agility: Each service can be developed, tested, and deployed independently, enabling faster development cycles.
- Fault Isolation: If one service fails, it doesn’t impact the entire system.
- Technology Diversity: Different services can use different technologies based on their specific requirements.
- Continuous Deployment: Services can be updated and deployed independently without affecting the entire application.
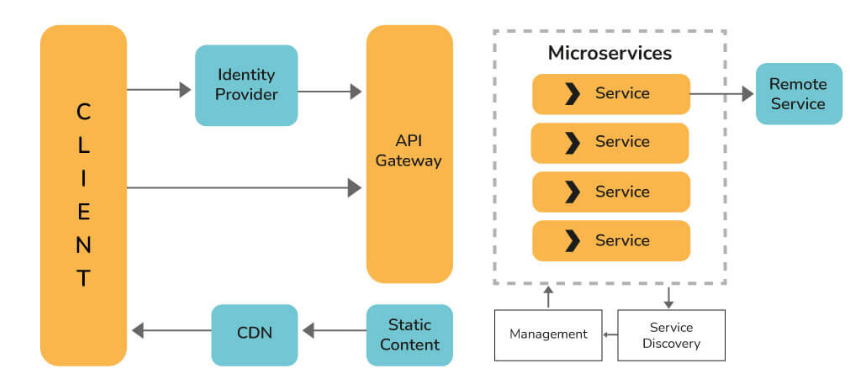
3. Explain the working of Microservice Architecture.
Microservice architectures consist of the following components:
- Clients: Requests from diverse users on different devices.
- Identity Provider: Validates user or client identity and issues security tokens.
- API Gateway: Handles client requests and acts as a central entry point.
- Static Content: Repository for the system’s content.
- Management: Balances services on nodes and detects failures.
- Service Discovery: Facilitates discovering communication routes between microservices.
- Content Delivery Network: A distributed network of proxy servers and data centers.
- Remote Service: Enables remote access to data or information on networked computers and devices.
4. How do microservices communicate with each other?
Microservices communicate with each other through lightweight protocols such as HTTP/REST or messaging systems like RabbitMQ or Apache Kafka. They can also use service discovery mechanisms to locate and connect to other services.
5. What is the difference between a monolithic architecture and a microservices architecture?
| Monolithic Architecture | Microservices Architecture |
|---|---|
| The monolithic architecture consists of a single, large application | Microservices architecture consists of small, loosely coupled services |
| All functionality is bundled together in a single codebase and deployed as a whole | Functionality is divided into independent services and deployed separately |
| Scaling is done by replicating the entire application | Scaling is done by scaling individual services independently |
| Changes or updates require the redeployment of the entire application | Changes or updates can be made to individual services without affecting others |
| Tightly coupled components and dependencies | Loosely coupled components and services |
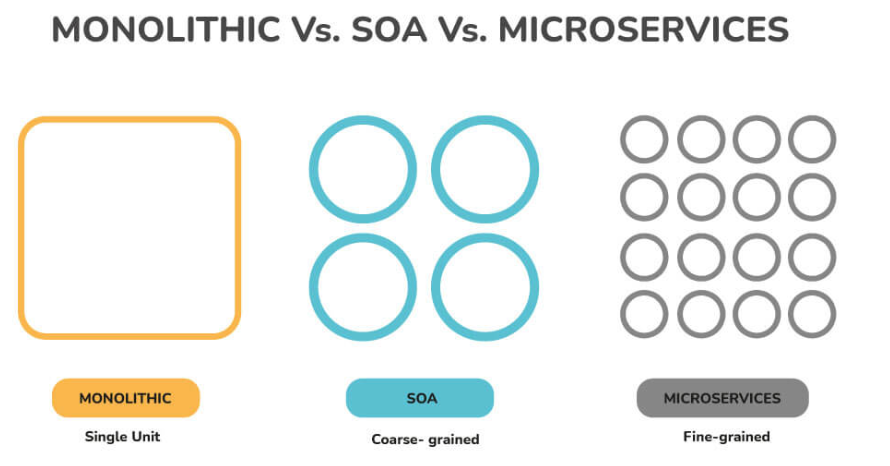
6. Write the difference between Monolithic, SOA, and Microservices Architecture.
Monolithic Architecture:
- All software components are tightly bundled together in a single system.
- One large system built with a unified codebase.
SOA (Service-Oriented Architecture):
- Group of services interacting or communicating with each other.
- Communication can range from simple data exchange to coordinated activities.
Microservice Architecture:
- Application structured as a cluster of small, autonomous services.
- Services deployed independently, scalable, and focused on specific business goals.
- Inter-service communication through standard protocols.
7. What is the role of an API gateway in a microservices architecture?
An API gateway acts as a single entry point for clients to access various microservices. It handles request routing, load balancing, and authentication, and can also provide features like rate limiting, caching, and request/response transformations.
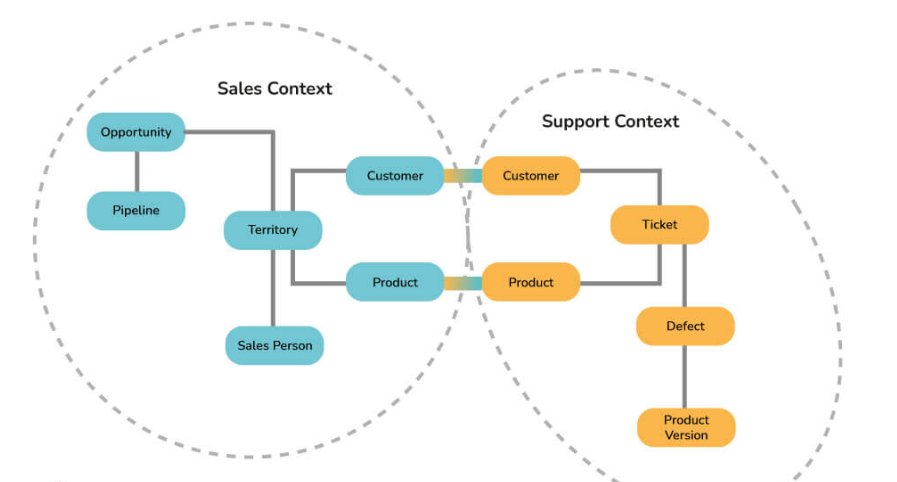
8. What do you mean by Bounded Context?
A Bounded Context plays a crucial role in Domain-Driven Design (DDD), serving as a key pattern for handling collaboration within extensive models and teams. DDD employs the practice of breaking down large models into multiple contexts, enabling better manageability. Moreover, it explicitly elucidates the relationships between these contexts. By adopting an object-oriented approach, this concept advocates the development of services closely tied to a specific data model, while also taking responsibility for maintaining the integrity and mutability of that data model.
9. Can you explain the concept of service discovery in microservices?
Service discovery is the process by which microservices dynamically locate and register with each other. It allows services to find and communicate with other services without hardcoding their network locations. Service discovery can be achieved using tools like Netflix Eureka, Consul, or Kubernetes’ service discovery mechanism.
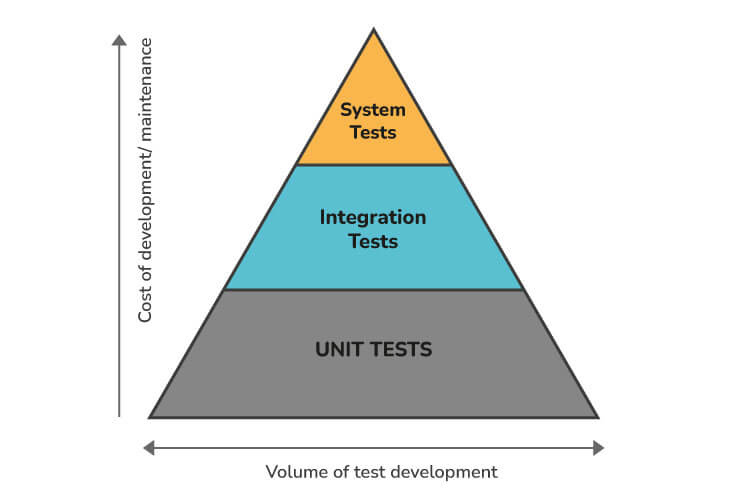
10. Explain the type of tests mostly used in Microservices.
As there are multiple microservices working together, microservice testing becomes quite complex when working with microservices. Consequently, tests are categorized according to their level:
Bottom-level tests:
- Technology-focused tests
- Includes unit tests and performance tests
- Fully automated process
Middle-level tests:
- Exploratory tests
- Involves stress tests and usability tests
Top-level tests:
- A limited number of acceptance tests
- Assist stakeholders in understanding and verifying software features
11. How does synchronous communication differ from asynchronous communication in a microservices architecture?
| Synchronous Communication | Asynchronous Communication |
|---|---|
| The caller waits for a response before proceeding | The caller doesn’t wait for an immediate response |
| Requires the caller and the callee to be available simultaneously | Caller and callee can operate independently and at different times |
| Provides immediate feedback and response | The response can be delayed or provided at a later time |
| Simpler to implement and reason about | More complex to implement and handle eventual consistency |
12. How do you ensure fault tolerance in a microservices architecture?
Fault tolerance in microservices can be achieved through various strategies, such as:
- Replication: Running multiple instances of a service to handle failures.
- Circuit Breaker pattern: Prevent cascading failures by breaking the communication to a failing service.
- Retry mechanisms: Automatically retrying failed requests to recover from temporary failures.
- Bulkhead pattern: Isolating failures to prevent them from impacting other services.
13. What are some common challenges in deploying and managing microservices?
Common challenges in deploying and managing microservices include:
- Service orchestration and coordination.
- Monitoring and observability across multiple services.
- Distributed tracing and debugging.
- Ensuring data consistency in distributed transactions.
- Managing dependencies between services.
- Deployment automation and versioning control.
14. What are the key differences between service orchestration and service choreography in a microservices ecosystem?
| Service Orchestration | Service Choreography |
|---|---|
| Centralized control and coordination of service interactions | Decentralized coordination of services through events or messages |
| A central component (orchestrator) dictates the flow and sequence of interactions | Services communicate directly with each other based on events or messages |
| Orchestrator defines the order and logic of service interactions | Services autonomously determine their interactions and behavior |
| Higher level of visibility and control | Lower coupling and higher service autonomy |
15. Explain Container in Microservices.
Containers are highly beneficial technologies for efficient resource allocation and sharing. They are widely regarded as the most effective and convenient approach for managing microservice-based applications during development and deployment. Docker, in particular, provides a powerful solution that allows you to package a microservice and its dependencies into a container image. This image can be easily utilized to deploy instances of the microservice whenever needed, eliminating the need for additional configuration or setup. With containers, you can encapsulate your microservices in portable and self-contained units, making it incredibly convenient to scale and manage them independently.
16. How do you handle data consistency across multiple microservices?
Data consistency in microservices can be handled through various approaches, including:
- Eventual consistency: Allowing temporary inconsistencies and resolving them asynchronously.
- Saga pattern: Using a series of compensating actions to maintain consistency in long-running transactions.
- Distributed transactions with two-phase commit (2PC) or three-phase commit (3PC).
- Event-driven architecture and event sourcing.
17. What is the role of containers in microservices deployment?
Containers provide a lightweight and isolated environment for deploying microservices. They encapsulate an application and its dependencies, making it easy to package, deploy, and scale microservices consistently across different environments. Containerization technologies like Docker are commonly used in microservices deployment.
18. How do you monitor and debug microservices in production?
Monitoring and debugging microservices can be challenging due to their distributed nature. Some common approaches include:
- Logging: Generating and collecting logs from each service and aggregating them for analysis.
- Distributed tracing: Capturing and correlating request traces across multiple services.
- Metrics and monitoring: Collecting performance metrics and monitoring system health using tools like Prometheus or Elasticsearch.
- Health checks: Implementing endpoints in each service to report its health status.
- APM (Application Performance Monitoring) tools: Using specialized tools like New Relic or Datadog for end-to-end monitoring and performance analysis.
19. What is the distinction between horizontal scaling and vertical scaling in the context of microservices?
| Horizontal Scaling | Vertical Scaling |
|---|---|
| Involves adding more instances of the same service | Involves increasing the resources (CPU, memory) of a single instance |
| Scalability is achieved by distributing the workload across multiple instances | Scalability is achieved by enhancing the capabilities of a single instance |
| Requires load balancing to distribute incoming requests | No load balancing is required as there is only one instance |
| Offers better fault tolerance as failures in one instance can be handled by others | Single point of failure as the entire service is hosted on a single instance |
20. Can you describe the process of scaling microservices?
Scaling microservices involves increasing the number of instances of a service to handle higher loads. It can be done horizontally (adding more instances) or vertically (increasing resources of existing instances). Scaling can be manual or automatic, triggered by metrics such as CPU usage or request rate. Load balancers or container orchestration platforms like Kubernetes are often used to distribute traffic across scaled instances.
21. How does data management differ in a shared database approach versus a database-per-service approach in microservices?
| Shared Database Approach | Database-per-Service Approach |
|---|---|
| Multiple services share a single database | Each service has its own dedicated database |
| Services can directly access and modify shared data | Services have exclusive control over their own data |
| Tighter coupling between services due to shared data dependencies | A looser coupling as services operate on their own data |
| Changes to the database schema or structure may impact multiple services | Each service can independently evolve its own database structure |
22. What strategies can be used for authentication and authorization in a microservices architecture?
Authentication and authorization in microservices can be implemented using various strategies, including:
- Token-based authentication: Using JWT (JSON Web Tokens) or OAuth for authentication and passing the token with each request.
- Centralized identity providers: Implementing a separate service for authentication and authorization, such as Keycloak or Okta.
- API gateways: Handling authentication and authorization at the gateway level before forwarding requests to microservices.
- Role-based access control (RBAC) or attribute-based access control (ABAC) mechanisms for fine-grained authorization.
23. What is the role of a service mesh in microservices communication?
A service mesh is a dedicated infrastructure layer that handles communication between services in a microservices architecture. It provides features like service discovery, load balancing, traffic management, security, and observability. Service meshes like Istio or Linkerd are often used to simplify and enhance the communication between microservices.
24. Can you explain the concept of event-driven architecture in the context of microservices?
Event-driven architecture (EDA) is an architectural pattern where services communicate by producing and consuming events. Events represent significant occurrences or state changes within the system. Microservices can publish events when something important happens, and other services can subscribe to those events to react accordingly. EDA enables loose coupling and scalability while supporting asynchronous and decoupled communication between services.
25. How do you handle versioning and backward compatibility in microservices?
Versioning and backward compatibility in microservices can be managed through strategies like:
- API versioning: Using different versions of APIs to introduce changes while maintaining backward compatibility for existing clients.
- Semantic versioning: Following a versioning scheme that indicates the impact of changes based on major, minor, and patch version numbers.
- API evolution: Designing APIs with extensibility in mind, allowing new fields or attributes to be added without breaking existing functionality.
- Supporting multiple versions concurrently during a transition period to give clients time to migrate.
26. What are some common patterns for inter-service communication in microservices?
Common patterns for inter-service communication in microservices include:
- Request-response: Synchronous communication using HTTP/REST or gRPC for real-time and point-to-point interactions.
- Publish-subscribe: Asynchronous communication through message brokers like RabbitMQ or Apache Kafka, where services publish events and other services subscribe to relevant events.
- Choreography: Services communicate directly with each other based on events and state changes, without a centralized orchestrator.
- Orchestration: A central service (orchestrator) coordinates and controls the flow of requests and responses among multiple services.
27. What are the differences between event sourcing and traditional database persistence in a microservices architecture?
| Event Sourcing | Traditional Database Persistence |
|---|---|
| Focuses on capturing and storing events as the source of truth | Focuses on storing the current state of the application |
| Allows reconstructing application state by replaying events | Stores the current state directly in the database |
| Enables audibility and historical tracking of application changes | Emphasizes the current state of the application |
| Provides a mechanism for event-driven communication and coordination | Relies on direct database access for data retrieval and updates |
28. How does the circuit breaker pattern work in microservices?
The circuit breaker pattern is used to handle failures and prevent cascading failures in a microservices architecture. It acts as a safety mechanism by monitoring the availability of a service. If the service fails repeatedly, the circuit breaker trips and subsequent requests are redirected to a fallback mechanism instead of continuously calling the failing service. This prevents resource exhaustion and allows the failing service to recover.
29. Can you describe the principles of domain-driven design and how it relates to microservices?
Domain-driven design (DDD) is an approach to software development that focuses on understanding and modeling the domain of the problem space. DDD emphasizes the collaboration between domain experts and software developers to create a rich, expressive domain model. In the context of microservices, DDD provides guidance on defining the boundaries of individual microservices based on distinct domain concepts or bounded contexts. Microservices can be designed to align with the different domains within an application, promoting modularity and maintainability.
30. How do you ensure transactional consistency across multiple microservices?
Ensuring transactional consistency across multiple microservices is challenging due to their distributed nature. Some approaches include:
- Saga pattern: Breaking a transaction into a series of smaller steps (local transactions) that can be compensated if any step fails, maintaining eventual consistency.
- Distributed transaction coordinator: Using a central coordinator or two-phase commit (2PC) protocol to coordinate and manage transactions across multiple services.
- Eventual consistency: Relaxing immediate consistency requirements and allowing data to be eventually consistent through asynchronous updates and compensating actions.
31. How does an API gateway differ from a service mesh in the context of microservices communication and management?
| API Gateway | Service Mesh |
|---|---|
| Acts as a single entry point for client requests | Manages communication between microservices at the network level |
| Handles routing, authentication, and API composition | Focuses on service-to-service communication and observability |
| Provides centralized control and management of APIs | Provides decentralized, sidecar-based control and management |
| Performs traffic shaping and load balancing | Offers advanced traffic management, security, and observability features |
32. What are some strategies for handling long-running processes in a microservices architecture?
Strategies for handling long-running processes in microservices include:
- Asynchronous messaging: Breaking down long-running processes into smaller steps and using messaging systems like RabbitMQ or Apache Kafka to coordinate and communicate between services.
- Choreography-based workflows: Defining workflows where services collaborate by reacting to events and state changes, allowing long-running processes to progress incrementally.
- Orchestration-based workflows: Using a central orchestrator service to manage the flow and coordination of long-running processes, ensuring their completion.
33. Can you explain the concept of CQRS (Command Query Responsibility Segregation) in microservices?
CQRS is an architectural pattern that separates read and write operations into separate models or services. In the context of microservices, CQRS allows optimizing the data models and operations specifically for reads (queries) and writes (commands). This can improve performance, scalability, and flexibility by allowing different services to handle different responsibilities based on the nature of the operation.
35. What are the contrasting characteristics of eventual consistency and strong consistency in microservices data handling?
| Eventual Consistency | Strong Consistency |
|---|---|
| Allows temporary inconsistencies and eventual synchronization | Ensures immediate consistency across all replicas or services |
| Provides higher availability and fault tolerance | Offers strong data integrity and accuracy |
| Can result in conflicts or conflicts resolution mechanisms | Minimizes conflicts and provides a single, consistent view of data |
| Requires mechanisms to handle data conflicts and eventual convergence | Ensures data is always in a consistent and coherent state |
36. How do you handle distributed caching in a microservices architecture?
Distributed caching in microservices can be handled through approaches like:
- Shared cache: Using a shared cache system like Redis or Memcached to store frequently accessed or computed data that can be shared across multiple microservices.
- Local caching: Each microservice maintains its own local cache to store and retrieve frequently accessed data specific to that service.
- Cache invalidation mechanisms: Implementing strategies to update or invalidate cached data when changes occur to maintain data consistency.
37. What are the differences between synchronous and asynchronous communication in microservices?
Synchronous communication in microservices is immediate and blocking, where the client waits for a response from the called service. Asynchronous communication, on the other hand, is non-blocking, and the client does not wait for a response immediately. Instead, it receives a callback or notification when the response is available. Asynchronous communication can improve system responsiveness, scalability, and fault tolerance but adds complexity in handling eventual consistency.
38. How do RESTful APIs and message queues differ in terms of communication patterns in a microservices architecture?
| RESTful APIs | Message Queues |
|---|---|
| Uses HTTP protocols and request-response communication | Uses messaging protocols and supports asynchronous communication |
| A request-response model with direct interaction between services | Decouples services and enables asynchronous communication |
| Provides synchronous and immediate communication | Provides asynchronous and decoupled communication |
| Well-suited for simple and real-time interactions | Well-suited for event-driven and loosely coupled interactions |
39. How can you define a RESTful endpoint in a Microservice using Spring Boot?
In Spring Boot, you can define a RESTful endpoint by annotating a method with @RequestMapping or @GetMapping and specifying the URL path.
40. What is the purpose of the @RequestBody annotation in Microservices development?
The @RequestBody annotation is used to bind the request body of an HTTP request to a method parameter in a Microservice.
41. How can you handle exceptions in a Microservice using Spring Boot?
Exceptions in Microservices can be handled by using the @ExceptionHandler annotation to define methods that handle specific exceptions.
42. Explain the usage of the @PathVariable annotation in Microservices.
The @PathVariable annotation is used to extract values from the URL path and bind them to method parameters in a Microservice.
43. What are the differences between fault tolerance and high availability strategies in a microservices ecosystem?
| Fault Tolerance | High Availability |
|---|---|
| Focuses on minimizing the impact of failures and recovering gracefully | Focuses on maximizing system uptime and providing uninterrupted service |
| Implements mechanisms like redundancy, replication, and fallbacks | Implements strategies like load balancing, failover, and disaster recovery |
| Emphasizes resilience and the ability to handle failures | Emphasizes continuous availability and minimizing downtime |
| Can tolerate individual service failures without affecting the system | Ensures the entire system is available and operational at all times |
44. How do you enable cross-origin resource sharing (CORS) in a Microservice developed with Spring Boot?
CORS can be enabled in a Spring Boot Microservice by using the @CrossOrigin annotation on controller classes or methods.
45. What is the purpose of the @RequestParam annotation in Microservices?
The @RequestParam annotation is used to bind request parameters from an HTTP request to method parameters in a Microservice.
46. How can you implement service discovery in a Microservice architecture?
Service discovery can be implemented in Microservices using tools like Netflix Eureka or HashiCorp Consul.
47. What is the role of the @RestController annotation in Microservices development?
The @RestController annotation is used to combine @Controller and @ResponseBody annotations, simplifying the development of RESTful Microservices.
48. Explain the usage of the @GetMapping annotation in Microservices.
The @GetMapping annotation is used to map HTTP GET requests to specific methods in a Microservice.
49. How can you implement authentication and authorization in a Microservice architecture?
Authentication and authorization can be implemented in Microservices using techniques such as OAuth 2.0, JWT (JSON Web Tokens), or integrating with an identity provider like Keycloak.
50. How can you ensure data privacy and security in a microservices architecture?
Data privacy and security in microservices can be ensured through practices such as:
- Securing communication: Using encryption protocols (HTTPS, TLS) for data transfer between services and enforcing authentication and authorization mechanisms.
- Access control: Implementing fine-grained access control policies and roles to restrict data access based on user privileges.
- Data encryption: Encrypting sensitive data at rest and implementing secure key management practices.
- Audit logging and monitoring: Recording and monitoring system activities to detect and respond to security threats or breaches.
To enhance your proficiency in Microservices Technical Interview Questions and gain a deeper understanding of the subject, the “Top 50 Microservices Interview Questions and Answers” is an invaluable resource catering to both beginners and experienced professionals. For comprehensive knowledge, you can visit freshersnow.com.



