
We’ve put together an extensive list of the Top 100 Networking Interview Questions and Answers on networking various topics. So, you don’t need to search any further.
★★ Latest Technical Interview Questions ★★
Networking Technical Interview Questions
Whether you’re a fresher or an experienced developer, this list covers the Top 100 Networking Interview Questions and Answers for both beginners and advanced technical interviews. Let’s delve into the realm of the Latest Networking Interview Questions and prepare to excel in Networking Technical Interview Questions.
Top 100 Networking Interview Questions and Answers
1. What is a network and how does it work?
A network is a group of interconnected devices that communicate with each other to share resources and data. It works by using communication protocols to enable devices to send and receive information across the network.
2. How are Network types classified?
Network types can be classified and divided based on the area of distribution of the network. The below diagram would help to understand the same:
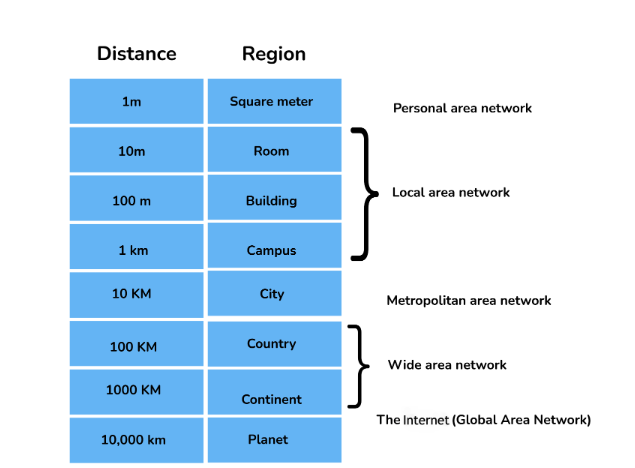
3. What is the difference between a LAN and a WAN?
A LAN (Local Area Network) is a network that covers a small geographical area such as an office, building, or campus. A WAN (Wide Area Network) covers a larger geographical area such as multiple cities or countries.
4. What is a router and how does it work?
A router is a networking device that connects multiple networks together and directs traffic between them. It works by analyzing incoming data packets and deciding which network they should be sent to.
5. What is the difference between TCP and UDP protocols?
| Parameter | TCP | UDP |
|---|---|---|
| Full form | Transmission Control Protocol | User Datagram Protocol |
| Connection | Connection-oriented | Connectionless |
| Message Delivery | Guaranteed | Non-guaranteed |
| Data Transfer | Reliable | Unreliable |
| Handshake | Three-way handshake | No handshake |
| Sequence | Maintains order of packets | No ordering |
| Congestion Control | Yes | No |
6. Explain LAN (Local Area Network)
Local Area Networks (LANs) are commonly utilized to connect computing devices and consumer electronics in order to share resources such as printers and fax machines, as well as exchange data. When LANs are implemented by companies or organizations, they are known as enterprise networks. LANs can be classified into two main types: wireless LANs, which utilize Wi-Fi technology and do not require cables for connections, and wired LANs, which use LAN cables for connections.
7. What is the syntax for setting a static IP address in Linux?
The syntax for setting a static IP address in Linux is:
sudo nano /etc/network/interfaces
Then add the following lines:
auto eth0 iface eth0 inet static address 192.168.1.100 netmask 255.255.255.0 gateway 192.168.1.1
8. What is a switch and how does it work?
A switch is a networking device that connects multiple devices together within a network. It works by forwarding data packets only to the intended recipient device.
9. What is a firewall and what is its purpose?
A firewall is a security device that monitors and filters incoming and outgoing network traffic based on predefined security rules. Its purpose is to protect the network from unauthorized access and malicious attacks.
10. Tell me something about VPN (Virtual Private Network)
A Virtual Private Network (VPN) is a type of private Wide Area Network (WAN) established over the public internet. It enables the creation of a secure tunnel or protected network between different networks using the internet as the medium of communication. Through the use of a VPN, a client can remotely connect to their organization’s network. The diagram below illustrates an example of an organizational WAN network in Australia that has been established using a VPN.
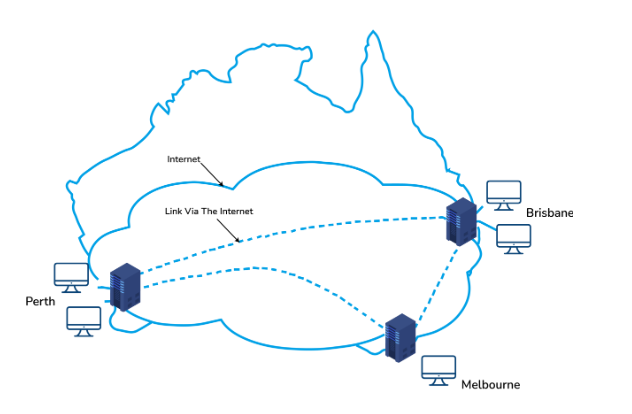
11. How does IPv4 differ from IPv6 in terms of addressing?
| Parameter | IPv4 | IPv6 |
|---|---|---|
| Address Size | 32 bits | 128 bits |
| Address Representation | Dotted Decimal Notation | Hexadecimal Notation |
| Address Configuration | Manual or DHCP | Manual, DHCPv6 or Stateless Address Autoconfig |
| Header Length | Fixed | Variable |
| Header Options | Limited | Extensive |
12. What is the OSI model and how is it used in networking?
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes communication protocols between devices on a network. It is used to ensure that devices from different vendors can communicate with each other by breaking down network communication into seven layers.
13. What is a protocol and give some examples?
A protocol is a set of rules that governs the communication between devices on a network. Examples of protocols include HTTP, FTP, TCP, IP, and SMTP.
14. What are nodes and links?
- Node: A node is any device within a network that can send or receive data and information. It serves as a point of intersection in a network and includes devices such as computers, laptops, printers, servers, modems, and more.
- Link: A link, also known as an edge, is the connection between two nodes in a network. It involves the type of connectivity, whether wired or wireless, between the nodes and the protocols used for communication between the nodes.
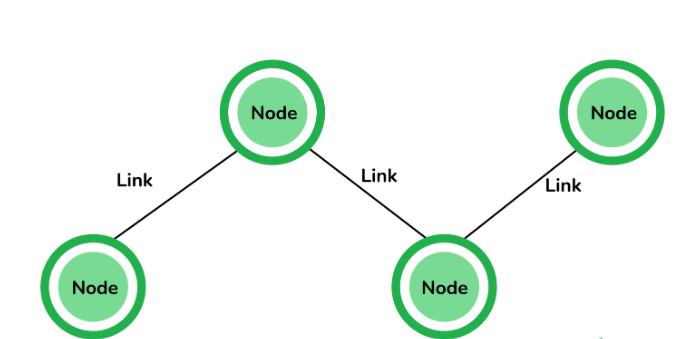
15. What is the syntax for displaying network interfaces in Windows using the command prompt?
The syntax for displaying network interfaces in Windows using the command prompt is:
ipconfig /all
16. What is the difference between TCP and UDP?
TCP (Transmission Control Protocol) is a connection-oriented protocol that guarantees the delivery of data packets, while UDP (User Datagram Protocol) is a connectionless protocol that does not guarantee the delivery of data packets.
17. What is an IP address and how is it assigned?
An IP (Internet Protocol) address is a unique numerical identifier assigned to every device on a network. It is assigned either manually by a network administrator or automatically by a DHCP server.
18. What distinguishes a hub from a switch in a network?
| Parameter | Hub | Switch |
|---|---|---|
| Functionality | Passes on received frames to all ports | Filters frames and forwards to specific ports |
| Broadcast Traffic | Sends to all ports simultaneously | Sends only to intended port(s) |
| Collision Domain | Single collision domain | Multiple collision domains |
| MAC Address Learning | No | Yes |
19. What is a subnet mask and how is it used?
Subnet mask:
- A subnet mask is a 32-bit number used to separate an IP address into network and host addresses.
- It is used in conjunction with IP addresses to determine the network and host portions of an IP address.
- A subnet mask is applied to an IP address using a bitwise AND operation.
20. What is a VLAN and how does it work?
VLAN:
- VLAN stands for Virtual Local Area Network.
- It is a logical grouping of devices in a network, regardless of their physical location.
- VLANs are used to segment a larger network into smaller, more manageable groups, and to increase network security.
21. What is the syntax for adding a new route in Linux?
The syntax for adding a new route in Linux is:
sudo ip route add <destination network>/<subnet mask> via <gateway IP address>
22. What is the difference between a router and a gateway?
| Parameter | Router | Gateway |
|---|---|---|
| Functionality | Connects different networks | Connects networks to the internet |
| Protocol Support | Network layer (Layer 3) | Application layer (Layer 7) |
| Address Translation | Translates IP addresses | Translates between IP addresses and other protocols (e.g. SIP, H.323) |
| Security and Firewall | Offers more security features | May have built-in firewall capabilities |
23. What is a VPN and how does it work?
VPN:
- VPN stands for Virtual Private Network.
- It is a secure connection between two or more devices over a public network, such as the Internet.
- VPNs are used to create a private network over a public network and to provide secure access to resources on the private network.
24. What is a proxy server and how does it work?
Proxy server:
- A proxy server is an intermediary server that acts as a gateway between a user and the Internet.
- It is used to provide anonymity, security, and caching services.
- When a user requests a web page, the request is sent to the proxy server, which then retrieves the web page and sends it back to the user.
25. What is the difference between symmetric and asymmetric encryption?
Symmetric vs asymmetric encryption:
- Symmetric encryption uses the same key to both encrypt and decrypt data.
- Asymmetric encryption uses two keys, a public key to encrypt data and a private key to decrypt it.
- Symmetric encryption is faster and more efficient for large amounts of data, while asymmetric encryption provides stronger security.
26. What is the syntax for displaying active network connections in Linux?
The syntax for displaying active network connections in Linux is:
sudo netstat -anp | grep ESTABLISHED
27. How do NAT and PAT differ in their handling of IP addresses?
| Parameter | NAT | PAT |
|---|---|---|
| Full form | Network Address Translation | Port Address Translation |
| Type of Address Translation | Changes the IP address only | Changes the IP address and port number |
| Port Management | Not applicable | Port number mapping is done dynamically |
28. What are SSL and TLS and how are they used in networking?
SSL and TLS:
- SSL stands for Secure Sockets Layer, and TLS stands for Transport Layer Security.
- They are cryptographic protocols used to provide secure communication over a network, typically the Internet.
- They are used to encrypt data between a web server and a client’s web browser, ensuring that sensitive information such as passwords and credit card numbers are protected from eavesdropping and interception.
29. What is SSH and how does it work?
SSH:
- SSH stands for Secure Shell.
- It is a protocol used to provide secure, encrypted communication between two computers over a network.
- SSH is commonly used for remote access to servers and for secure file transfers.
30. What is FTP and how does it work?
FTP:
- FTP stands for File Transfer Protocol.
- It is a protocol used for transferring files between computers over a network.
- FTP is commonly used for uploading and downloading files to and from web servers.
31. What is HTTP and how does it work?
- HTTP:
- HTTP stands for Hypertext Transfer Protocol.
- It is a protocol used for transmitting data over the Internet.
- HTTP is the foundation of data communication for the World Wide Web.
32. What is SMTP and how does it work?
SMTP:
- SMTP stands for Simple Mail Transfer Protocol.
- It is a protocol used for sending and receiving email over the Internet.
- SMTP is used to send email from a client to a mail server, and from one mail server to another.
33. What is the syntax for configuring a network interface with DHCP in Linux?
The syntax for configuring a network interface with DHCP in Linux is:
sudo nano /etc/network/interfaces
Then add the following lines:
auto eth0 iface eth0 inet dhcp
34. What are POP and IMAP and how do they work?
POP and IMAP:
- POP stands for Post Office Protocol, and IMAP stands for Internet Message Access Protocol.
- They are protocols used for retrieving email from a mail server.
- POP downloads email from the server to the client’s device, while IMAP allows the client to view and manipulate email on the server.
35. What distinguishes a LAN from a WAN in terms of coverage and connectivity?
| Parameter | LAN | WAN |
|---|---|---|
| Coverage | Small geographical area, e.g. office, building | Large geographical area, e.g. country, continent |
| Connectivity | High-speed, wired and wireless connections | Slower speed, long-distance connections |
| Ownership | Privately owned | Publicly or privately owned |
36. What is VoIP and how does it work?
VoIP:
- VoIP stands for Voice over Internet Protocol.
- It is a technology used for transmitting voice and other multimedia content over the Internet.
- VoIP is commonly used for phone and video conferencing and is an alternative to traditional phone services.
37. What is DNS and how does it work?
DNS (Domain Name System) is a system that translates domain names into IP addresses so that devices can locate each other on a network. It works by maintaining a database of domain names and their corresponding IP addresses.
38. What is DHCP and how does it work?
DHCP (Dynamic Host Configuration Protocol) is a network protocol that automatically assigns IP addresses and other network configuration parameters to devices on a network. It works by having a DHCP server distribute IP addresses to devices that request them.
39. What is the syntax for checking the connectivity of a network device in Windows?
The syntax for checking the connectivity of a network device in Windows is:
ping <IP address>
40. What is NAT and how does it work?
NAT (Network Address Translation) is a process that allows devices on a private network to access the internet using a single public IP address. It works by translating private IP addresses into a single public IP address when communicating with the internet.
41. How does a firewall differ from an intrusion detection system in network security?
| Parameter | Firewall | Intrusion Detection System |
|---|---|---|
| Functionality | Filters incoming and outgoing traffic | Analyzes traffic patterns to detect attacks |
| Placement | Network boundary, e.g. between LAN and WAN | Within the network, e.g. on a server |
| Action | Blocks or allows traffic based on predefined rules | Alerts |
42. What is QoS and how does it work?
QoS (Quality of Service) is a set of techniques used to prioritize network traffic based on the type of traffic and its importance. It works by assigning different levels of priority to different types of traffic to ensure that critical traffic gets the necessary bandwidth.
43. What is the syntax for displaying the routing table in Linux?
The syntax for displaying the routing table in Linux is:
sudo route -n
44. What is SNMP and how does it work?
SNMP (Simple Network Management Protocol) is a protocol used to manage and monitor devices on a network. It works by allowing network administrators to query devices for information such as status and performance metrics.
45. What is the syntax for displaying network information in macOS using the command line?
The syntax for displaying network information in macOS using the command line is:
ifconfig -a
46. What is ARP and how does it work?
ARP (Address Resolution Protocol) is a protocol used to map IP addresses to MAC addresses on a network. It works by broadcasting a request to all devices on the network to determine the MAC address of a specific IP address.
47. What is RARP and how does it work?
RARP (Reverse Address Resolution Protocol) is a protocol used to map MAC addresses to IP addresses on a network. It works by broadcasting a request to all devices on the network to determine the IP address of a specific MAC address.
48. What is the difference between a static and dynamic IP address?
| Parameter | Static IP Address | Dynamic IP Address |
|---|---|---|
| Address Assignment | Manually assigned by a network administrator | Assigned by DHCP server on the network |
| Address Changes | Remains the same unless changed manually | Changes periodically or when the lease expires |
| Network Configuration | More complex configurations required | Simpler configuration with DHCP server |
| Security | Less secure due to the static nature | More secure due to frequent changes |
49. What is ICMP and how does it work?
ICMP (Internet Control Message Protocol) is a protocol used to send error messages and operational information about network conditions. It works by sending messages between devices to provide feedback about the status of the network.
50. What is the syntax for configuring a static route in Windows?
The syntax for configuring a static route in Windows is:
route add <destination network> mask <subnet mask> <gateway IP address>
51. What is OSPF and how does it work?
OSPF (Open Shortest Path First) is a routing protocol used to determine the best path for data packets to travel across a network. It works by analyzing the network topology and calculating the shortest path between devices.
52. What is BGP and how does it work?
BGP (Border Gateway Protocol) is a routing protocol used to exchange routing information between networks on the internet. It works by allowing network administrators to control the flow of traffic between networks by defining routing policies.
53. What is EIGRP and how does it work?
EIGRP (Enhanced Interior Gateway Routing Protocol) is a routing protocol used to determine the best path for data packets to travel within a network. It works by using a metric to calculate the shortest path between devices and sharing this information with neighboring devices.
54. What is the syntax for checking network connectivity in Linux?
The syntax for checking network connectivity in Linux is:
ping <IP address>
55. How does SSL differ from TLS in terms of security features and encryption algorithms?
| Parameter | SSL | TLS |
|---|---|---|
| Full form | Secure Socket Layer | Transport Layer Security |
| Encryption Algorithms | Uses RSA and Diffie-Hellman key exchange | Uses more advanced encryption algorithms (e.g. AES, Camellia) |
| Security Features | Vulnerable to attacks such as POODLE and BEAST | More secure due to improved cipher suites and authentication methods |
| Protocol Support | Up to version 3.0 | Versions 1.0 to 1.3 |
56. What is MPLS and how does it work?
MPLS (Multiprotocol Label Switching) is a technique used to improve the speed and efficiency of network traffic. It works by assigning labels to data packets and using these labels to forward packets along predefined paths across the network.
57. What is STP and how does it work?
STP (Spanning Tree Protocol) is a protocol used to prevent loops in a network topology. It works by allowing devices to elect a root bridge and creating a tree-like structure for network traffic to follow.
58. What is VTP and how does it work?
VTP (VLAN Trunking Protocol) is a protocol used to manage VLANs (Virtual Local Area Networks) on a network. It works by allowing network administrators to configure VLANs on a central switch and then propagate these configurations to other switches on the network.
59. What is HSRP and how does it work?
HSRP (Hot Standby Router Protocol) is a protocol used to provide redundancy for network devices such as routers. It works by allowing multiple routers to share a virtual IP address and automatically electing a primary router to handle network traffic.
60. What distinguishes a virtual private network (VPN) from a leased line connection in network access and security?
| Parameter | VPN | Leased Line Connection |
|---|---|---|
| Network Access | Uses public network infrastructure | Dedicated private line |
| Security | Uses encryption and tunneling protocols | Security measures depend on the provider |
| Cost | Cost-effective due to shared public infrastructure | More expensive due to dedicated line rental |
| Scalability | Easy to scale up or down based on the need | Limited scalability |
61. What is the syntax for configuring a network interface with a static IP address in Windows?
The syntax for configuring a network interface with a static IP address in Windows is:
netsh interface ipv4 set address <interface name> static <IP address> <subnet mask> <gateway IP address>```
62. What is VRRP and how does it work?
VRRP (Virtual Router Redundancy Protocol) is a protocol used to provide redundancy for network devices such as routers. It works by allowing multiple routers to share a virtual IP address and automatically electing a primary router to handle network traffic if the primary router fails.
63. What is GLBP and how does it work?
- GLBP stands for Gateway Load Balancing Protocol, which is a Cisco proprietary protocol that allows multiple routers to share the same virtual IP address as the default gateway for a network.
- It works by distributing traffic among multiple routers that are configured to be part of the same GLBP group. One router is elected as the active virtual gateway (AVG), while others are standby virtual gateways (SVGs).
- The AVG is responsible for forwarding packets sent to the virtual IP address, while the SVGs back up the AVG in case of failure.
- GLBP also supports load balancing, where traffic is distributed among multiple active virtual forwarders (AVFs) on the same subnet.
64. What is NAT and how does it work?
- NAT stands for Network Address Translation, which is a technique used to map one or more private IP addresses to a public IP address.
- It works by modifying the source and/or destination IP address of IP packets as they pass through a router or firewall.
- NAT can be used to conserve public IP addresses by allowing multiple devices with private IP addresses to share a single public IP address.
- NAT also provides a degree of security by hiding the internal network structure from the public Internet.
65. What is the syntax for displaying the MAC address of a network interface in Windows?
The syntax for displaying the MAC address of a network interface in Windows is:
ipconfig /all | findstr /C:"Physical Address"
66. What is PAT and how does it work?
- PAT stands for Port Address Translation, which is a type of NAT that allows multiple devices to share a single public IP address by using different port numbers.
- It works by modifying the source port number of outgoing packets to a unique port number and then modifying it back to the original port number when the response is received.
- PAT is commonly used in residential and small business networks, where a single public IP address is assigned by the Internet service provider (ISP) and needs to be shared by multiple devices.
67. What is NTP and how does it work?
- NTP stands for Network Time Protocol, which is used to synchronize the clocks of computers and other devices on a network.
- It works by exchanging time information between NTP servers and clients, with the servers providing more accurate time information to the clients.
- NTP uses a hierarchical system of time sources, with stratum 0 servers providing the most accurate time information and stratum 16 servers providing the least accurate time information.
- NTP can be used to maintain accurate time for applications that rely on synchronized clocks, such as financial transactions and scientific experiments.
68. What is RADIUS and how does it work?
- RADIUS stands for Remote Authentication Dial-In User Service, which is a networking protocol used to provide centralized authentication, authorization, and accounting (AAA) for remote access clients.
- It works by sending authentication requests from a remote access client to a RADIUS server, which then verifies the user’s credentials and sends back a response indicating whether the authentication was successful.
- RADIUS can also be used for authorization and accounting purposes, such as controlling access to network resources and keeping track of usage statistics.
- RADIUS is commonly used in enterprise networks to provide secure remote access to employees and other authorized users.
69. What is TACACS+ and how does it work?
- TACACS+ stands for Terminal Access Controller Access-Control System Plus, which is a networking protocol used to provide centralized authentication, authorization, and accounting (AAA) for network devices.
- It works by sending authentication requests from a network device to a TACACS+ server, which then verifies the user’s credentials and sends back a response indicating whether the authentication was successful.
- TACACS+ can also be used for authorization and accounting purposes, such as controlling access to network resources and keeping track of usage statistics.
70. What is a port and how is it used in networking?
A port is a logical construct that identifies a specific process or service running on a computer in a network. Ports are used to facilitate communication between different devices on a network by assigning unique numbers to different types of traffic, such as email or web traffic. Ports allow multiple network applications to operate simultaneously without interfering with each other.
71. What is a socket and how is it used in networking?
A socket is an endpoint of a two-way communication link between two programs running on a network. It is used to enable communication between a client and a server on a network. A socket includes an IP address and a port number, and it facilitates data transfer between two applications.
72. What is an SYN flood attack and how is it prevented?
An SYN flood attack is a type of DoS (Denial-of-Service) attack that sends a large number of connection requests with fake IP addresses to a server, overwhelming it with traffic and preventing legitimate traffic from getting through. To prevent SYN flood attacks, network administrators can implement several measures such as limiting the number of connection requests from a single IP address, using firewalls to block suspicious traffic, or implementing SYN cookies, which allow the server to validate connection requests before opening a connection.
73. What is a DDoS attack and how is it prevented?
A DDoS (Distributed Denial-of-Service) attack is a type of cyber attack that floods a network or server with traffic from multiple sources, causing it to crash or become inaccessible. To prevent DDoS attacks, network administrators can use techniques such as traffic filtering, rate limiting, and using specialized DDoS protection services to detect and mitigate attacks in real time.
74. What is the syntax for configuring a DNS server in Linux?
The syntax for configuring a DNS server in Linux is:
sudo nano /etc/resolv.conf
Then add the following line:
nameserver <DNS server IP address>
75. What is a man-in-the-middle attack and how is it prevented?
A man-in-the-middle (MITM) attack is a type of cyber attack in which an attacker intercepts communication between two parties on a network, often for the purpose of stealing sensitive information. To prevent MitM attacks, network administrators can use measures such as end-to-end encryption, digital signatures, and SSL/TLS protocols to secure network communication and detect any attempts to tamper with data in transit.
76. What is a brute-force attack and how is it prevented?
A brute-force attack is a type of cyber attack in which an attacker uses automated tools to repeatedly try different passwords or encryption keys until the correct one is found. To prevent brute-force attacks, network administrators can use measures such as implementing strong passwords, using multi-factor authentication, limiting login attempts, and detecting and blocking repeated failed login attempts.
77. What is a phishing attack and how is it prevented?
A phishing attack is a type of social engineering attack in which an attacker sends fraudulent emails or messages, often impersonating a legitimate entity, in order to trick the victim into providing sensitive information or downloading malware. To prevent phishing attacks, users can be trained to recognize and report suspicious emails, and network administrators can use measures such as email filtering and blocking malicious websites to detect and prevent phishing attempts.
78. What is a ransomware attack and how is it prevented?
A ransomware attack is a type of cyber attack in which an attacker encrypts the victim’s files or system and demands payment in exchange for the decryption key. To prevent ransomware attacks, network administrators can use measures such as keeping the software and operating systems up-to-date, implementing security patches, using antivirus software, and backing up data regularly.
79. What is the syntax for releasing and renewing a DHCP lease in Windows?
The syntax for releasing and renewing a DHCP lease in Windows is:
ipconfig /release ipconfig /renew
80. What is a botnet and how is it prevented?
A botnet is a network of compromised computers that are controlled by a single attacker for malicious purposes, such as launching DDoS attacks or stealing sensitive information. To prevent botnet attacks, network administrators can use measures such as implementing strong passwords, limiting access to network resources, and monitoring network activity for signs of botnet activity.
81. What is a vulnerability and how is it identified and remediated?
A vulnerability is a weakness in a computer system or network that can be exploited by attackers to gain unauthorized access or steal sensitive information. Vulnerabilities can be identified through various methods such as vulnerability scanning and penetration testing. Once a vulnerability is identified, network administrators can remediate it by applying security patches, updating software, and implementing access controls to limit the attack surface.
82. What is network segmentation and why is it important?
Network segmentation is the process of dividing a network into smaller sub-networks, or segments, to improve security and performance. By segmenting a network, network administrators can limit the spread of cyber attacks and improve network performance by controlling the flow of traffic between different segments.
83. What is network virtualization and how is it implemented?
Network virtualization is the process of creating virtual networks that are independent of the physical network infrastructure, allowing multiple virtual networks to run on a single physical network. Network virtualization is implemented through the use of virtual network devices such as virtual switches and routers, which can be programmed to control network traffic between virtual networks.
84. What is the syntax for displaying the network interface statistics in Linux?
The syntax for displaying the network interface statistics in Linux is:
sudo netstat -i```
85. What is network monitoring and how is it performed?
Network monitoring is the process of monitoring network activity to detect and respond to security threats and performance issues. Network monitoring is performed through various tools and techniques such as packet sniffing, log analysis, and intrusion detection systems, which allow network administrators to monitor network traffic, detect suspicious activity, and respond to security incidents in real time.
86. What is DLP and how does it work?
DLP, or Data Loss Prevention, is a security measure that aims to prevent sensitive data from leaving an organization’s network. It works by monitoring data in transit or at rest and enforcing policies to prevent unauthorized access, copying, or transmission of sensitive information.
87. What is SIEM and how does it work?
SIEM, or Security Information and Event Management, is a security tool that collects and analyzes security-related data from various sources in real time. It works by aggregating logs and events from network devices, servers, applications, and other sources and using algorithms to detect and alert security incidents.
88. What is the syntax for displaying the TCP/IP configuration in Windows?
The syntax for displaying the TCP/IP configuration in Windows is:
ipconfig /all
89. What is UEBA and how does it work?
UEBA, or User and Entity Behavior Analytics, is a security technology that uses machine learning algorithms to identify abnormal behavior patterns of users and entities in a network. It works by analyzing historical and real-time data from multiple sources, such as logs, events, and network traffic, to detect anomalies and potential security threats.
90. What is SDN and how does it work?
SDN, or Software-Defined Networking, is a network architecture that separates the network control plane from the data plane. It works by centralizing network management and programmatically controlling the flow of data packets using software-based controllers.
91. What is NFV and how does it work?
NFV, or Network Function Virtualization, is a network architecture that replaces dedicated hardware devices with software-based virtual network functions. It works by using virtualization technology to consolidate and abstract network functions, such as firewalls, routers, and load balancers, onto commodity servers.
92. What is VxLAN and how does it work?
VxLAN, or Virtual Extensible LAN, is a network virtualization technology that extends Layer 2 segments over an IP-based network. It works by encapsulating Layer 2 frames in Layer 3 packets and using a virtual network identifier (VNI) to identify the virtual network.
93. What is the syntax for configuring a network interface with a VLAN tag in Linux?
The syntax for configuring a network interface with a VLAN tag in Linux is:
sudo nano /etc/network/interfaces
Then add the following lines:
auto eth0.10 iface eth0.10 inet dhcp vlan-raw-device eth0
94. What is a packet and how does it travel through a network?
A packet is a unit of data that is transmitted over a network. It travels through the network by being encapsulated in various layers of headers and trailers as it passes through each network device until it reaches its destination.
95. What is a frame and how does it travel through a network?
A frame is a unit of data that is transmitted over a network at the data link layer (Layer 2). It travels through the network by being encapsulated in various layers of headers and trailers as it passes through each network device until it reaches its destination.
96. What is a segment and how does it travel through a network?
A segment is a unit of data that is transmitted over a network at the transport layer. It travels through the network by being encapsulated in various layers of headers and trailers as it passes through each network device until it reaches its destination.
97. What is a byte and how does it travel through a network?
A byte is a unit of data that consists of 8 bits. It travels through the network as part of packets, frames, or segments, being encapsulated in various layers of headers and trailers as it passes through each network device until it reaches its destination.
98. What is the syntax for displaying the ARP table in Linux?
The syntax for displaying the ARP table in Linux is:
sudo arp -a
99. What is a bit and how does it travel through a network?
A bit is the smallest unit of data in a computer network. It travels through the network as part of packets, frames, or segments, being encapsulated in various layers of headers and trailers as it passes through each network device until it reaches its destination.
100. What is bandwidth and how does it affect network performance?
Bandwidth is the maximum amount of data that can be transmitted over a network in a given time period. It affects network performance by determining how much data can be transferred at any given time. A network with high bandwidth can transfer more data in a shorter period of time, resulting in faster performance and better user experience.
Freshers and experienced professionals looking to excel in technical interviews can benefit greatly from the insights provided by our Top 100 Networking interview questions and answers. By following us at freshersnow.com, you can expand your knowledge and stay up-to-date on the Networking Interview Questions for Freshers and developments in the field of networking.



