
Web API Interview Questions and Answers: When it comes to landing a job in the tech industry, technical interviews are a crucial part of the hiring process. If you’re looking to apply for a role that involves Web API development, it’s important to prepare for the interview by brushing up on the latest Web API interview questions. This article features the top 100 Web API interview questions and answers, covering a range of topics including technical skills, best practices, and problem-solving abilities.
★★ Latest Technical Interview Questions ★★
Web API Technical Interview Questions
Whether you’re a seasoned professional or a fresher just starting out in your career, these Web API Interview Questions for Freshers will help you prepare for your next interview with confidence.
Top 100 Web API Interview Questions and Answers
1. What is a Web API and how does it differ from other APIs?
- The Web API (Application Programming Interface), as its name implies, is an interface that can be accessed over the web via the HTTP protocol. It is an excellent platform for exposing data and services to various different systems. It provides a mechanism for sending data to a server and allows access to it by server code. It can be developed using various technologies, such as Java, ASP.NET, and others.
- Web APIs typically use JSON or XML for data exchange, while other APIs may use different formats such as binary or text.
2. How do you handle authentication and authorization in a Web API?
- Authentication is the process of verifying the identity of a user, while authorization determines whether a user has access to a particular resource.
- Common authentication methods for Web APIs include OAuth2 and JSON Web Tokens (JWTs).
- Authorization can be handled using role-based access control or by defining specific permissions for each resource.
3. What is the difference between HTTP GET and POST requests, and when should each be used in API design?
| HTTP Method | GET | POST |
|---|---|---|
| Request Parameters | Parameters are included in the query string of the URL | Parameters are included in the body of the request |
| Request Size | Limited by the maximum length of a URL | Not limited, but generally limited by server settings |
| Idempotent | Yes | No |
| Caching | Responses can be cached | Responses cannot be cached |
| Security | Data is visible in the URL and can be intercepted | Data is hidden in the request body and less likely to be intercepted |
| Usage | Used for read-only operations, retrieving data | Used for write operations, submitting data |
4. What HTTP methods are commonly used in Web APIs, and what do they represent?
- The most commonly used HTTP methods in Web APIs are GET, POST, PUT, PATCH, and DELETE.
- GET is used to retrieve a resource, POST is used to create a new resource, PUT is used to update an existing resource, PATCH is used to partially update a resource, and DELETE is used to delete a resource.
5. How do you handle error responses in a Web API?
- Error responses should include an appropriate HTTP status code, such as 400 for bad requests or 404 for not found.
- Error messages should provide useful information to the client, but should not reveal sensitive information.
- It is also helpful to provide a standardized error format to make it easier for clients to handle errors.
6. Why is the Web API important?
- The Web API provides data or information from the server and is widely used for the following reasons:
- It offers an interface for websites and client applications to access data.
- It can access data from the database and save data back to it.
- It supports different text formats such as XML, JSON, etc.
- It is compatible with any type of browser and device, including mobile, desktop, and web.
- It uses low bandwidth, such as XML or JSON data, making it suitable for devices with limited bandwidth, such as smartphones.
- From a business perspective, Web API is more applicable for UI/UX, increases interest in the company’s products and services, and increases website traffic.
7. How do you handle versioning in a Web API?
- Versioning can be handled by including the version number in the URL or using custom HTTP headers.
- It is important to have a clear versioning strategy to ensure compatibility with older clients and to communicate changes to the API.
8. What is the syntax for making a GET request in a Web API?
The syntax for making a GET request in a Web API is as follows:
| GET /api/{controller}/{id} |
9. What are the benefits of using a RESTful API?
- RESTful APIs are designed to be simple, scalable, and easily understood.
- They use standard HTTP methods and data formats, making them easy to integrate with other systems.
- RESTful APIs are also flexible, allowing clients to access resources in a variety of ways.
10. How do you design a scalable Web API?
- To design a scalable Web API, it is important to use caching and load balancing to distribute traffic across multiple servers.
- APIs should also be designed to be stateless, meaning that each request should contain all the information needed to complete the request.
- It is also important to monitor performance and make adjustments as necessary to ensure scalability.
11. How do you handle caching in a Web API?
- Caching can be used to improve performance by storing frequently accessed resources in memory.
- It is important to set appropriate cache headers to ensure that clients receive the most up-to-date data.
- Caching can also be used to reduce the load on the server and improve scalability.
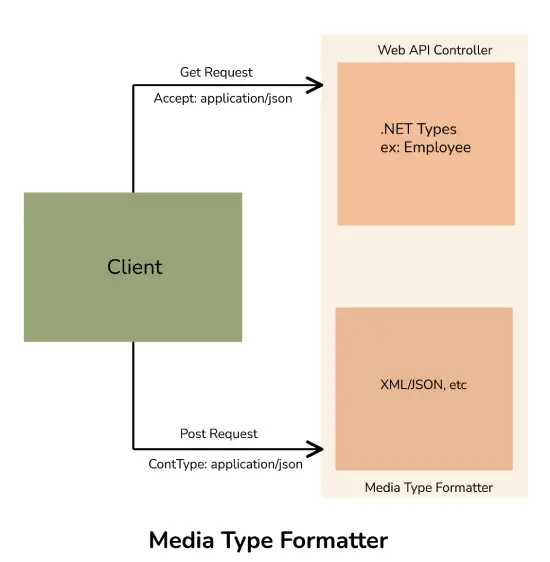
12. What are media type formatters?
In a Web API, media type formatters are a set of classes that play a crucial role in serializing data. Serialization refers to the process of translating data into a format that can be transmitted and reconstructed later. By serializing request/response data, Web API can better understand the request data format and send data in a format that the client expects. This ensures that the data is exchanged efficiently and effectively between client and server in a Web API. Media type formatters simply specify the data being transferred between the client and server in HTTP response or request.
There are various types of media type formatters in a Web API, and each one is responsible for handling a specific data format. The following table shows some commonly used media type formatters along with their corresponding MIME types:
| Media Type Formatter Class | MIME Type | Description |
|---|---|---|
| JsonMediaTypeFormatter | application/json, text/json | Handles JSON format |
| XmlMediaTypeFormatter | application/xml, text/json | Handles XML format |
| FormUrlEncodedMediaTypeFormatter | application/x-www-form-urlencoded | Handles HTML form URL-encoded data |
| JQueryMvcFormUrlEncodedFormatter | application/x-www-form-urlencoded | Handles model-bound HTML form URL-encoded data |
13. What is a resource in a Web API?
- A resource is any entity that can be accessed and manipulated through a Web API, such as a user, a product, or a blog post.
- Each resource should have a unique identifier, such as a URL or an ID number, and should be represented in a consistent format.
14. How do you handle concurrency and consistency in a Web API?
- Concurrency can be handled by using locking mechanisms or optimistic concurrency control.
- Consistency can be ensured by using transactions or by using a database with strong consistency guarantees.
- It is also important to design APIs to be idempotent, meaning that repeating a request will not have unintended consequences.
15. What is the syntax for making a POST request in a Web API?
The syntax for making a POST request in a Web API is as follows:
| POST /api/{controller} |
16. What is the difference between API versioning through URL and header, and which approach do you prefer?
| API Versioning | URL | Header |
|---|---|---|
| Implementation | Version number is included in the URL | Version number is included in a custom header |
| Visibility | Version number is visible in the URL | Version number is hidden in the header |
| Caching | Different versions of the same endpoint can be cached separately | Caching is more complex, as responses can vary based on the version number |
| Ease of Use | Easy to implement and understand | More complex to implement and requires custom code for handling the version header |
| Backward Compatibility | Easy to maintain backward compatibility with older clients | More complex to maintain backward compatibility |
17. How do you secure a Web API?
- Use HTTPS to encrypt data in transit
- Implement authentication mechanisms like OAuth, JWT or API keys
- Use SSL/TLS certificates to ensure secure connections
- Validate and sanitize user input to prevent injection attacks
- Implement access control mechanisms to restrict access to certain resources
- Regularly update and patch software to prevent security vulnerabilities
18. What are the common content types used in a Web API?
- JSON (JavaScript Object Notation)
- XML (Extensible Markup Language)
- Plain text
- HTML (Hypertext Markup Language)
- Image formats like PNG, JPEG, GIF
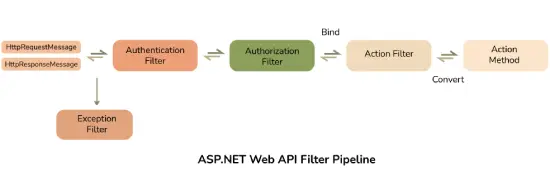
19. What are Web API filters?
Filters in Web API are used to add extra logic at different levels of request processing.
Different types of filters available in Web API are:
- Authentication Filter: It authenticates HTTP requests and checks the identity of the user.
- Authorization Filter: It handles authorization and checks if the user is authenticated. If not, it returns an HTTP status code 401 without invoking the action.
- AuthorizeAttribute: It is a built-in authorization filter provided by Web API.
- Action Filter: It is an attribute that can be applied to a controller action or the entire controller. It adds extra logic before or after the controller action executes.
- Exception Filter: It is used to handle unhandled exceptions in Web API. It is implemented using the “IExceptionFilter” interface.
- Override Filter: It is used to exclude specific action methods or controllers from the global filter or controller level filter. It modifies the behavior of other filters for individual action methods.
20. How do you handle pagination in a Web API?
- Use query parameters like “page” and “limit” to control the number of results returned
- Return a “next” link in the response headers to allow clients to request the next page
- Use “offset” and “limit” parameters to specify the starting index and number of results to return
- Return the total number of results in the response to help clients navigate the results.
21. How do you handle cross-origin resource sharing (CORS) in a Web API?
- Set the “Access-Control-Allow-Origin” header to specify which domains are allowed to access the API
- Use preflight requests to check if the requesting domain is allowed to access the API
- Implement authentication mechanisms to restrict access to certain resources
- Use SSL/TLS certificates to ensure secure connections
22. What is the syntax for including query parameters in a Web API request?
The syntax for including query parameters in a Web API request is as follows:
| /api/{controller}?param1=value1¶m2=value2 |
23. How do you implement rate limiting in a Web API?
- Set a limit on the number of requests a client can make in a certain period of time
- Use API keys to track usage and limit access to certain resources
- Use a distributed cache to store request data and prevent abuse
- Return HTTP 429 status code when the rate limit is exceeded.
24. What is HATEOAS and how is it implemented in a Web API?
- HATEOAS (Hypermedia As The Engine Of Application State) is a constraint of REST that allows clients to navigate a Web API through hyperlinks in responses.
- A Web API can implement HATEOAS by returning links to related resources in the response body, which clients can use to discover and navigate other parts of the API.
25. How do you handle file uploads in a Web API?
- Use HTTP POST method with “multipart/form-data” content type to upload files
- Limit file size and type to prevent abuse and security risks
- Use authentication mechanisms to restrict access to certain resources
- Use SSL/TLS certificates to ensure secure connections
26. What is the difference between MVC and Web API?
| Aspect | MVC | Web API |
|---|---|---|
| Purpose | Used for building web applications that reply as both data and views | Used for building HTTP services that reply only as data |
| Data formats | Returns data in JSON format by using JsonResult | Returns data in different formats such as JSON, XML, etc |
| Content negotiation | Supports content negotiation | Does not support content negotiation |
| Self-hosting | Supports self-hosting | Does not support self-hosting |
| RESTful services | Not very helpful in creating RESTful services | Very helpful in creating RESTful services |
| Response | Returns a view (HTML) | Returns REST responses |
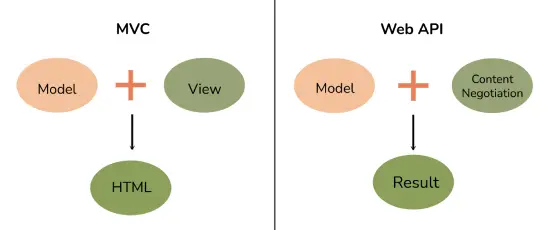
27. What are the different types of data formats that can be used in a Web API?
- JSON (JavaScript Object Notation)
- XML (Extensible Markup Language)
- Plain text
- HTML (Hypertext Markup Language)
- Image formats like PNG, JPEG, GIF
28. How do you handle request and response headers in a Web API?
- Use headers to pass additional information between client and server, like authentication tokens or content type
- Validate and sanitize header values to prevent injection attacks
- Set appropriate status codes and response headers to indicate success or failure
29. What is the difference between API authentication and authorization, and what are some common approaches for each?
| API Security | Authentication | Authorization |
|---|---|---|
| Definition | Verification of user identity | Determination of user access rights |
| Example | User logs in with username and password | User is granted specific permissions based on their role or group |
| Implementation | Credentials are sent with each request | Permissions are checked before allowing access to a resource |
| Common Approaches | Basic Authentication, OAuth, API Keys | Role-based Access Control, Attribute-based Access Control |
30. What is the syntax for specifying the HTTP status code in a Web API response?
The syntax for specifying the HTTP status code in a Web API response is as follows:
| return StatusCode(200); |
31. What is the difference between synchronous and asynchronous communication in a Web API?
- Synchronous communication blocks the client until a response is received, while asynchronous communication allows the client to continue processing while waiting for a response.
- Synchronous communication is simpler to implement but can lead to performance issues if requests take a long time to complete, while asynchronous communication can be more complex but allows for better scalability and responsiveness.
32. What are the advantages of using JSON over XML in a Web API?
- JSON is lightweight and more efficient in transmitting data over the network compared to XML.
- JSON is easier to read and understand by humans, while XML is verbose and complex.
- JSON can be easily parsed and manipulated by most programming languages, making it a popular choice for Web APIs.
- JSON has a simpler data structure and requires fewer tags than XML, making it more suitable for complex data structures.
- JSON is widely used in modern web development and has become a de facto standard for data exchange.
33. How do you handle compression in a Web API?
- Gzip compression is a popular method for compressing responses in a Web API.
- It is important to set the “Accept-Encoding” header in the client request to indicate that the client can accept compressed responses.
- The server can check the “Accept-Encoding” header in the request and compress the response using Gzip before sending it back to the client.
- Compression can significantly reduce the size of the response and improve the performance of the Web API.
34. What is the difference between SOAP and RESTful APIs?
- SOAP is a protocol for exchanging structured data over the internet, while RESTful is a style of web architecture that uses HTTP and other web standards.
- SOAP uses XML for data exchange, while RESTful uses JSON or other lightweight data formats.
- SOAP requires a dedicated server and client to interpret the messages, while RESTful is more flexible and can be implemented using simple HTTP requests.
- SOAP has more features and is often used in enterprise applications, while RESTful is more suitable for simpler, web-based applications.
35. What is the difference between JSON and XML, and which one should be used for API payloads?
| JSON | XML |
|---|---|
| Stands for | JavaScript Object Notation |
| Data representation | Uses a key-value pair structure to represent data |
| Readability | Easier to read and write for humans |
| Parsing | Parsing is faster and easier compared to XML |
| Size | JSON payloads are typically smaller than XML payloads, resulting in faster data transfer |
| Support | Widely supported by modern programming languages and platforms |
| Usage | Commonly used in Web APIs |
36. How do you handle routing in a Web API?
- Routing maps URLs to specific actions or methods in a Web API.
- The routing configuration is typically defined in a routing table or file.
- Routing can be based on the HTTP method, request parameters, or other factors.
- In ASP.NET Web API, routing is defined using attributes on the controller and action methods.
37. What is the syntax for returning JSON data in a Web API response?
The syntax for returning JSON data in a Web API response is as follows:
| return Json(data); |
38. How do you handle content negotiation in a Web API?
- Content negotiation is the process of selecting the most appropriate response format based on the client’s preferences and capabilities.
- The client can indicate its preferred format using the “Accept” header in the request.
- The server can examine the “Accept” header and select the appropriate response format.
- In ASP.NET Web API, content negotiation is handled by the “ContentNegotiator” class.
39. What is the difference between idempotent and non-idempotent methods in a Web API?
- Idempotent methods can be called multiple times without changing the state of the system or resource, while non-idempotent methods may change the state with each call.
- GET, HEAD, and OPTIONS are idempotent methods in a Web API, while POST, PUT, PATCH, DELETE are non-idempotent methods.
- Idempotent methods are safer to use in certain scenarios, such as retrying failed requests or handling network errors.
40. How do you handle timeouts in a Web API?
- A timeout occurs when the server takes too long to respond to a client request.
- The client can set a timeout value in the request to limit the waiting time.
- The server can also set a timeout value to limit the processing time of the request.
- In ASP.NET Web API, timeouts can be configured using the “HttpConfiguration” class.
41. How do you handle long-running operations in a Web API?
- Long-running operations can cause timeouts and other performance issues in a Web API.
- One approach is to use asynchronous programming to execute the long-running operation in the background while allowing the Web API to respond to other requests.
- Another approach is to use background workers or queues to handle long -running operations outside the context of the Web API.
- In ASP.NET Web API, long-running operations can be implemented using async/await or background tasks.
42. How do you handle database transactions in a Web API?
- Database transactions ensure that a set of database operations are performed atomically, meaning that either all the operations succeed or none of them do.
- In a Web API, database transactions can be handled using a database transaction object or by using an ORM (Object Relational Mapping) framework.
- Transactions can be initiated using the “TransactionScope” class in .NET or by starting a transaction on the database connection.
- It is important to handle exceptions and rollback transactions if an error occurs during the transaction.
43. How do you handle concurrency in a Web API?
- Concurrency refers to the issue of multiple users accessing the same resource or data simultaneously, which can lead to conflicts and data integrity issues.
- In a Web API, concurrency can be handled using optimistic or pessimistic locking.
- Optimistic locking assumes that conflicts are rare and allows multiple users to access the same resource concurrently, but checks for conflicts when updates are made.
- Pessimistic locking assumes that conflicts are common and locks the resource to prevent other users from accessing it while it is being used.
- In ASP.NET Web API, concurrency can be handled using optimistic concurrency control mechanisms like ETags and version numbers.
44. What is the difference between API rate limiting and throttling, and how do you implement each in your application?
| Aspect | API Rate Limiting | API Throttling |
|---|---|---|
| Purpose | To limit the number of requests a client can make within a specific time frame | To limit the rate at which requests are made by a client |
| Implementation | Usually done by setting a maximum number of requests a client can make within a certain time period (e.g. 100 requests per hour) | Usually done by setting a maximum rate at which a client can make requests (e.g. 10 requests per second) |
| Result | Once the client reaches the limit, the API may block further requests or return an error response code | The API may delay requests that exceed the rate limit, or return an error response code |
| Use Case | Useful for preventing abuse or DoS attacks, and ensuring fair use of resources among clients | Useful for managing server load and ensuring that server resources are not overwhelmed by client requests |
| Implementation Example | Using middleware like ASP.NET Core’s RateLimit package or third-party services like Cloudflare or Akamai |
Using tools like nginx, or implementing custom rate limiting logic within the API codebase |
45. What is the syntax for defining a route prefix in a Web API controller?
The syntax for defining a route prefix in a Web API controller is as follows:
| [RoutePrefix(“api/users”)] |
46. How do you implement client-side caching in a Web API?
- Client-side caching can be implemented by setting appropriate caching headers in the API response.
- The headers can be set using middleware or directly in the controller action.
- The headers include Cache-Control, ETag, Last-Modified, and Expires.
- The caching can be configured to be time-based or event-based depending on the requirements.
- The caching can be invalidated based on user actions or time-based expiration.
47. What are the benefits of using API gateways?
- API gateways provide a centralized entry point for all API requests.
- They help in load balancing and scaling of the API services.
- They provide security features like authentication and authorization.
- They can be used for monitoring and analytics of the API usage.
- They help in reducing the complexity of the client-side code by providing a unified interface to the API services.
- They enable API versioning and allow for easy upgrades and changes to the API services.
48. How do you implement search functionality in a Web API?
- Search functionality can be implemented by accepting search parameters in the API request.
- The search parameters can be passed as query string parameters or as part of the request body.
- The search can be implemented using a database query or by using a search engine like Elasticsearch.
- The search results can be returned as JSON objects or as part of a paged response.
- The search functionality can be optimized by using indexing and caching techniques.
49. What are the best practices for handling user input in a Web API?
- User input should be validated on both the client and server sides.
- The input validation should be performed as early as possible in the API request processing pipeline.
- The input validation should include checking for data type, length, and format.
- The API should return appropriate error messages for invalid input.
- The API should use HTTPS to encrypt the input data during transmission.
- The API should avoid exposing sensitive information in error messages.
50. What is the syntax for creating a custom route in a Web API controller?
The syntax for creating a custom route in a Web API controller is as follows:
| [Route(“api/users/{id}”)] |
51. How do you handle data validation in a Web API?
- Data validation can be performed using model binding or by manually validating the input data.
- Model binding automatically maps the request data to the corresponding model properties and performs validation based on the model annotations.
- Manual validation can be performed by checking the request data against a set of validation rules.
- The API should return appropriate error messages for invalid data.
- The API should use HTTPS to encrypt the data during transmission.
- The API should avoid exposing sensitive information in error messages.
52. What is the difference between RESTful API and GraphQL, and when should you use one over the other?
| RESTful API | GraphQL | |
|---|---|---|
| Request structure | Each endpoint corresponds to a specific resource or action | A single endpoint allows for complex, nested queries |
| Data format | Uses a fixed data structure (JSON, XML, etc.) | Allows clients to request specific data fields and structures |
| Caching | Supports caching to improve performance | No built-in caching, but can be implemented at the server or client level |
| Versioning | Typically requires versioning of endpoints to maintain backwards compatibility | No need for versioning since clients can request only the data they need |
| Error handling | Uses HTTP status codes to indicate errors | Returns a predictable error object in the response |
| Tooling | Many existing tools and frameworks support RESTful APIs | Still evolving, but has some specialized tools and libraries available |
| Use cases | Best for CRUD operations and simple, resource-based interactions | Best for complex queries and scenarios where minimizing network requests is important |
53. How do you handle error logging and tracing in a Web API?
- Error logging can be implemented using a logging framework like log4net or NLog.
- The logging can be configured to capture both server-side and client-side errors.
- The logging should capture relevant information like the error message, stack trace, and request details.
- The API should use correlation IDs to trace the request flow across multiple API services.
- The API should provide a mechanism to log errors to a centralized location for easy monitoring and analysis.
54. What are the best practices for documentation in a Web API?
- The API documentation should be comprehensive and up-to-date.
- The documentation should include information about the API endpoints, request and response formats, and error messages.
- The documentation should provide examples and use cases for the API usage.
- The documentation should be available in both HTML and PDF formats.
- The documentation should be versioned along with the API.
- The API should provide a mechanism to generate and publish the documentation automatically.
55. What is the difference between HTTP and HTTPS, and why is it important for a Web API?
- HTTP is an unencrypted protocol that sends data in plaintext, whereas HTTPS is a secure protocol that encrypts the data during transmission.
- HTTPS provides protection against eaves dropping, man-in-the-middle attacks, and other security threats.
- HTTPS uses SSL/TLS certificates to establish a secure connection between the client and the server.
- Web APIs should always use HTTPS to ensure the security and privacy of the data being transmitted.
- Using HTTPS can also improve the SEO ranking of the API by signaling to search engines that the API is secure.
56. What is the syntax for specifying the HTTP method in a Web API action method?
The syntax for specifying the HTTP method in a Web API action method is as follows:
| [HttpGet] public IHttpActionResult GetUser(int id) |
57. What is a middleware in a Web API?
- Middleware is a software component that sits between the client and the server in the API request processing pipeline.
- Middleware can perform a variety of tasks like authentication, caching, logging, and error handling.
- Middleware can be added to the pipeline using the UseMiddleware method in the Startup class.
- Middleware can be ordered based on their execution order using the Use method in the Startup class.
- Middleware can be custom-built or can be obtained from third-party libraries.
58. How do you handle authentication and authorization using OAuth 2.0 in a Web API?
- OAuth 2.0 is an authorization framework that allows users to grant third-party applications access to their resources without revealing their passwords.
- OAuth 2.0 uses access tokens to grant authorization to the API services.
- The API can implement OAuth 2.0 using the Authorization Server and Resource Server patterns.
- The Authorization Server issues access tokens to the client after the user has authorized the client to access their resources.
- The Resource Server verifies the access token and allows the client to access the protected resources.
- The API should use HTTPS to encrypt the access tokens during transmission.
59. What are the different types of security threats to a Web API?
- Common security threats to a Web API include injection attacks, cross-site scripting (XSS), cross-site request forgery (CSRF), and unauthorized access.
- Injection attacks involve inserting malicious code into API requests or responses.
- XSS attacks involve injecting malicious scripts into web pages accessed by users.
- CSRF attacks involve tricking a user into performing an action on a website without their knowledge or consent.
- Unauthorized access can occur if an attacker gains access to API keys or authentication tokens.
60. What is the difference between API testing and API monitoring, and how do you ensure the reliability of your API?
| Aspect | API Testing | API Monitoring |
|---|---|---|
| Purpose | To ensure the API functions correctly and as expected during development and before deployment | To detect performance issues and ensure the API functions correctly in production |
| Timing | Occurs before deployment or during development | Occurs after deployment, during production |
| Scope | Usually focuses on a specific functionality or feature of the API | Monitors the entire API for performance and functionality |
| Approach | Testing is conducted manually or using automated testing tools | Monitoring is usually automated using monitoring tools |
| Results | Results of testing are used to improve the API before deployment | Results of monitoring are used to detect and resolve issues in production |
| Metrics | Metrics measured may include response time, error rate, throughput, and functional accuracy | Metrics measured may include response time, availability, uptime, and error rate |
| Frequency | Testing is conducted periodically or when new features are added to the API | Monitoring is conducted continuously or periodically, depending on the severity of the application |
| Benefits | Helps detect bugs and issues early in the development cycle | Helps detect issues in production before they affect users, improving user experience and reducing downtime |
| Tools | Common testing tools include Postman, JUnit, and REST Assured | Common monitoring tools include Datadog, New Relic, and Prometheus |
61. How do you handle load balancing in a Web API?
- Load balancing can be handled using a variety of techniques, including round-robin DNS, hardware load balancers, and software load balancers such as NGINX or HAProxy.
- Load balancing can also be performed at different layers of the network stack, such as at the application layer or the transport layer.
- It is important to monitor performance and adjust load balancing settings as necessary to ensure optimal performance.
62. What are the best practices for error handling in a Web API?
- Error messages should be informative and clear, but should not reveal sensitive information.
- Error responses should include an appropriate HTTP status code, such as 400 for bad requests or 404 for not found.
- It is helpful to provide a standardized error format to make it easier for clients to handle errors.
- It is also important to log errors for debugging purposes.
63. What is the difference between a microservice and a Web API?
- A microservice is a small, independent service that performs a specific function within a larger application.
- A Web API is an interface that allows applications to communicate with each other over the internet using HTTP.
- While a Web API may be used to expose a microservice, a microservice can also be accessed using other means such as message queues or direct method calls.
64. How do you handle serialization and deserialization in a Web API?
- Serialization is the process of converting an object into a format that can be transmitted over the network, such as JSON or XML.
- Deserialization is the process of converting the transmitted data back into an object.
- Most Web API frameworks include built-in support for serialization and deserialization, but it is important to ensure that the serialization format is compatible with the client.
65. What is the syntax for binding HTTP request parameters to a Web API action method?
The syntax for binding HTTP request parameters to a Web API action method is as follows:
| public IHttpActionResult UpdateUser([FromBody] User user) |
66. How do you handle concurrency and locking in a Web API?
- Concurrency can be handled by using locking mechanisms or optimistic concurrency control.
- Locking mechanisms involve blocking access to a resource while it is being updated by another request.
- Optimistic concurrency control involves checking whether a resource has been modified since it was last accessed and rejecting the request if it has.
- It is important to monitor performance and adjust locking settings as necessary to ensure optimal performance.
67. What is the difference between a PUT and PATCH request in a Web API?
- PUT requests are used to update an entire resource, while PATCH requests are used to update a portion of a resource.
- PUT requests require that the entire resource be sent in the request body, while PATCH requests only require the updated fields to be sent.
- PUT requests are idempotent, meaning that repeating the request will have the same result, while PATCH requests may not be idempotent.
68. How do you handle API versioning in a microservice architecture?
- API versioning can be handled by including the version number in the URL or using custom HTTP headers.
- It is important to have a clear versioning strategy to ensure compatibility with older clients and to communicate changes to the API.
- In a microservice architecture, each microservice may have its own versioning scheme, so it is important to ensure that all the services are compatible with each other.
69. How do you handle data migration in a Web API?
- Data migration can be a complex and time-consuming process, especially if the API has a large amount of data.
- It is important to have a clear plan for data migration, including identifying which data needs to be migrated and how to handle any data that cannot be migrated.
- It may be necessary to perform data migration in stages to minimize disruption to the API.
- It is also important to test the API thoroughly after data migration to ensure that it is functioning correctly.
70. What is the difference between a Web API and a web service?
- A Web API is a specific type of web service that uses HTTP to expose an interface that allows applications to communicate with each other over the internet.
- Web services may use other protocols, such as SOAP or XML-RPC, to expose an interface.
- Web APIs are typically designed to be lightweight and easy to use, while web services may be more complex and require more configuration.
71. How do you handle data encryption in a Web API?
- Use HTTPS to encrypt data in transit
- Implement encryption mechanisms like SSL/TLS to encrypt data at rest
- Use secure key management practices to protect encryption keys
- Encrypt sensitive data before storing it in databases or other storage systems
- Regularly update and patch software to prevent security vulnerabilities
72. What is a service mesh and how is it used in a Web API?
- A service mesh is a layer of infrastructure that manages communication between microservices in a distributed system.
- It can be used in a Web API to provide features like service discovery, load balancing, traffic management, and security.
73. How do you handle load testing in a Web API?
- Use tools like Apache JMeter, Gatling, or LoadRunner to simulate user traffic and measure response times and throughput
- Test with realistic scenarios and data sets to identify performance bottlenecks
- Use performance metrics like CPU usage, memory usage, and network latency to optimize performance
- Scale horizontally to handle increased traffic during peak periods
74. What are the best practices for designing the API schema in a Web API?
- Use a consistent naming convention for endpoints, resources, and parameters
- Use HTTP verbs to map operations to resources
- Use versioning to manage changes to the API
- Use appropriate status codes and response formats to indicate success or failure
- Use pagination to manage large result sets
- Use authentication and authorization mechanisms to secure the API
- Use consistent error handling to provide meaningful feedback to clients
75. How do you implement API documentation using OpenAPI?
- Use the OpenAPI specification to describe the API endpoints, resources, parameters, and responses
- Use tools like Swagger or ReDoc to generate interactive documentation from the OpenAPI specification
- Keep the documentation up-to-date as the API changes
76. What is the syntax for enabling CORS in a Web API project?
The syntax for enabling CORS in a Web API project is as follows:
| config.EnableCors(); |
77. What are the best practices for API versioning?
- Use a consistent versioning scheme, like “v1”, “v2”, etc.
- Use versioning to manage changes to the API without breaking existing clients
- Use versioning to deprecate old functionality and introduce new features
- Provide clear documentation and communication about versioning changes
- Use API gateways or proxies to manage multiple versions of the API
78. How do you handle data transformation in a Web API?
- Use serialization and deserialization to convert between internal data structures and external data formats like JSON or XML
- Use libraries or frameworks that support data transformation, like Jackson for JSON or JAXB for XML
- Use appropriate data formats and serialization techniques to optimize performance and reduce network overhead
79. How do you handle partial responses in a Web API?
- Use query parameters like “fields” to allow clients to request only the fields they need
- Use appropriate response formats like JSON or XML to support partial responses
- Use pagination to manage large result sets and reduce the amount of data returned in each response
80. What is a webhook and how is it used in a Web API?
- A webhook is a mechanism for triggering events in response to changes in data or state.
- It can be used in a Web API to notify clients of changes in resources, like new data being added or existing data being updated.
- Clients can register a webhook URL with the API, which will be called whenever the corresponding event occurs.
81. How do you implement serverless architecture for a Web API?
- Use a serverless platform like AWS Lambda or Azure Functions to host the API code
- Use API gateways or proxies to manage requests and responses
- Use serverless databases like AWS DynamoDB or Azure Cosmos DB to store and retrieve data
- Use serverless authentication and authorization mechanisms like AWS Cognito or Azure Active Directory to secure the API
- Use serverless monitoring and logging tools to track API usage, performance, and errors
- Design the API to be stateless, with all necessary data passed in the request or retrieved from external sources
- Use appropriate tools and frameworks for building serverless APIs, like the Serverless Framework or AWS SAM.
82. How do you handle data security in a Web API?
- Security is an important aspect of a Web API as it can be accessed over the internet, which makes it vulnerable to attacks.
- Data security can be handled by implementing authentication and authorization mechanisms such as OAuth2, JWT, or OpenID Connect.
- Additional security measures can be implemented such as TLS/SSL encryption, input validation, rate limiting, and API key authentication.
83. How do you implement message queuing in a Web API?
- Message queuing is a technique used to decouple the sender and receiver of a message, allowing for asynchronous communication.
- In a Web API, message queuing can be implemented using technologies like RabbitMQ, Azure Service Bus, or Amazon SQS.
- The Web API can publish messages to a message queue, and consumers can then subscribe to the queue to receive the messages.
84. How do you handle request/response validation in a Web API?
- Request/response validation is the process of verifying that the data sent to and received from a Web API is valid and meets certain criteria.
- In a Web API, validation can be implemented using data annotations, regular expressions, or custom validators.
- The Web API can return validation errors to the client in a consistent format, such as a JSON object.
85. How do you handle API governance in a Web API?
- API governance refers to the set of policies, procedures, and guidelines that govern the use and development of a Web API.
- Governance can be implemented using tools like API gateways or API management platforms, which provide features such as access control, rate limiting, and analytics.
- Governance policies can be defined to enforce standards for API design, documentation, and testing.
86. How do you handle API testing and automation in a Web API?
- API testing is the process of verifying that a Web API functions as intended.
- Testing can be automated using tools like Postman, Swagger, or NUnit.
- Automated tests can be integrated into a continuous integration/continuous delivery (CI/CD) pipeline to ensure that changes to the API do not introduce regressions or bugs.
87. What are the best practices for API documentation in a Web API?
- API documentation is important for ensuring that developers can understand how to use a Web API.
- Best practices for API documentation include using a consistent format, providing examples, documenting error codes, and providing a sandbox environment for testing.
- Tools like Swagger or API Blueprint can be used to generate documentation automatically.
88. How do you handle distributed tracing in a Web API?
- Distributed tracing is the process of tracking a request as it passes through multiple services or components.
- In a Web API, distributed tracing can be implemented using tools like Zipkin, Jaeger, or Application Insights.
- Tracing information can be passed between services using HTTP headers, and a central tracing server can be used to aggregate and visualize the trace data.
89. What is the difference between a public and private Web API?
- A public Web API is accessible over the internet and can be used by anyone with an internet connection and appropriate authentication.
- A private Web API is accessible only within a private network or to specific authorized users.
- Public Web APIs are typically used for integrating with third-party applications or exposing functionality to a wide audience, while private Web APIs are used for internal or partner use cases.
90. How do you implement API versioning using URL parameters?
- API versioning is the process of maintaining multiple versions of a Web API to support backward compatibility and changes in functionality.
- URL parameters can be used to specify the version of the API that the client is calling.
- For example, the URL “api.example.com/v1/users” would call version 1 of the API, while “api.example.com/v2/users” would call version 2 of the API.
91. How do you handle fault tolerance in a Web API?
- Fault tolerance refers to the ability of a Web API to continue functioning even in the presence of failures or errors.
- Fault tolerance can be implemented using techniques like redundancy, circuit breaking, and retry policies.
- For example, multiple instances of the API can be deployed across different servers or data centers to provide redundancy, while circuit breaking can be used to isolate failing components and prevent cascading failures.
92. How do you implement API monitoring in a Web API?
- API monitoring involves monitoring the API’s performance, uptime, and response times to ensure it’s meeting service level agreements (SLAs).
- API monitoring can be implemented using third-party monitoring tools like Pingdom, New Relic, and Datadog.
- API monitoring can also be implemented using custom monitoring scripts that periodically send requests to the API and check its response times and status codes.
- Monitoring can be performed on different levels like server-side, client-side, and network-level monitoring.
- API monitoring can also involve logging the API’s activities and analyzing the logs to detect errors and performance issues.
93. What is the difference between a monolithic and microservice architecture, and which is better for a Web API?
- Monolithic architecture is a traditional architecture where all the application’s components are tightly coupled and run on a single server.
- Microservice architecture is a modern architecture where the application is split into small, independent services that can be deployed and scaled independently.
- Microservice architecture is better suited for Web APIs as it allows for better scalability, fault tolerance, and flexibility.
- Monolithic architecture is simpler to implement and maintain but can become complex and difficult to scale as the application grows.
94. How do you handle load balancing using a proxy server in a Web API?
- Load balancing involves distributing incoming traffic across multiple servers to improve performance, availability, and reliability.
- A proxy server can be used to implement load balancing in a Web API.
- The proxy server can distribute incoming traffic across multiple API servers using round-robin or other load balancing algorithms.
- The proxy server can also handle caching, SSL termination, and other tasks.
- Load balancing can be implemented using open-source tools like Nginx, Apache, and HAProxy.
95. How do you handle API security using JSON Web Tokens (JWT)?
- JSON Web Tokens (JWT) are an open standard for secure token-based authentication and authorization.
- JWTs are used to securely transmit information between parties as a JSON object.
- JWTs consist of three parts: a header, a payload, and a signature.
- JWTs can be used for authentication, authorization, and information exchange between the API and the client.
- JWTs can be used in conjunction with HTTPS to provide end-to-end encryption and security.
96. How do you implement API versioning using custom headers?
- API versioning is the practice of creating multiple versions of an API to support different clients and use cases.
- API versioning can be implemented using custom headers.
- The API can specify the version of the API using a custom header like X-API-Version.
- The client can specify the version of the API it wants to use using the same custom header.
- The API can route the requests to the appropriate version of the API based on the custom header.
97. What is the difference between synchronous and asynchronous APIs?
- Synchronous APIs block the client until a response is received from the server.
- Asynchronous APIs allow the client to continue with other tasks while waiting for a response from the server.
- Asynchronous APIs can improve performance, scalability, and user experience by reducing wait times.
- Synchronous APIs are simpler to implement but can become a bottleneck as the API grows.
98. How do you handle database transactions in a distributed Web API?
- Database transactions involve a group of database operations that are executed as a single unit of work.
- Distributed Web APIs can handle database transactions using the Two-Phase Commit (2PC) protocol.
- 2PC involves a coordinator that coordinates the transaction between the different database servers.
- The coordinator sends a prepare message to all the servers to verify if they can execute the transaction.
- If all the servers respond with a yes, the coordinator sends a commitmessage to all the servers to commit the transaction.
- If any server responds with a no, the coordinator sends an abort message to all the servers to roll back the transaction.
99. How do you handle database sharding in a Web API?
- Database sharding involves splitting a database into multiple smaller databases to improve scalability and performance.
- Web APIs can handle database sharding by partitioning the data across multiple database servers based on a shard key.
- The shard key is a unique identifier that is used to partition the data.
- The API can route requests to the appropriate shard based on the shard key.
- Database sharding can improve scalability, availability, and performance but can also add complexity to the API.
100. How do you handle API performance and optimization in a Web API?
- API performance and optimization involve improving the API’s response times, throughput, and efficiency.
- API performance can be improved by optimizing the API’s code, caching, and database queries.
- API performance can also be improved by using asynchronous processing, load balancing, and horizontal scaling.
- API optimization involves minimizing the API’s response size, reducing the number of requests, and using compression and minification.
- API performance can be monitored using tools like New Relic, Datadog, and Pingdom.
The 100 Web API Interview Questions and Answers provide a comprehensive guide to prepare for technical interviews, from fresher to seasoned professionals. To acquire further knowledge, follow us at freshersnow.com.



